- August 10, 2023
- Posted by: team SOUTECH
- Category: Blog, Cyber-security and Ethical Hacking Training, Ethical Hacking and Kali Linux Free Training, Security, Technologies
Network discovery and enumeration are processes used in cybersecurity to identify and gather information about devices, services, and resources within a computer network. Discovery involves mapping the network topology, while enumeration involves actively probing devices to obtain details such as open ports, running services, and user accounts, which can aid in vulnerability assessment and attack planning.
Case Study: A security consultant is hired to assess the security posture of a company’s network infrastructure. The consultant conducts network scanning and enumeration activities using Nmap and OpenVAS. They perform passive reconnaissance to gather information about the company’s network architecture, public-facing devices, and services. With active scanning and enumeration techniques, the consultant identifies live hosts, open ports, and specific services running on those ports. The collected data is then analyzed to identify potential security weaknesses and recommendations for improvement.
Step-by-step instructions:
1. Define the scope: Determine the target network or system you have permission to scan and enumerate. Clearly establish the scope of the reconnaissance activities.
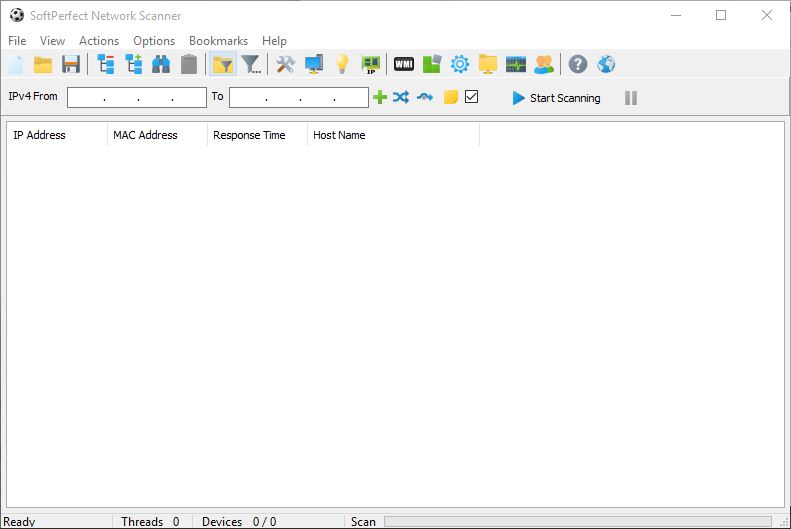
2. Choose network scanning tools: Select appropriate network scanning tools such as Nmap (https://nmap.org/) or OpenVAS (https://www.openvas.org/) to assist with the scanning and enumeration process.
3. Conduct network discovery:
a. Begin with passive reconnaissance techniques, such as publicly available information or search engine queries, to gather information about the target network or organization.
b. Use tools like Shodan (https://www.shodan.io/) to identify publicly accessible devices and services associated with the target.
4. Perform active network scanning:
a. Utilize network scanning tools to identify live hosts and open ports within the target network.
b. Conduct port scanning to identify services running on each open port.
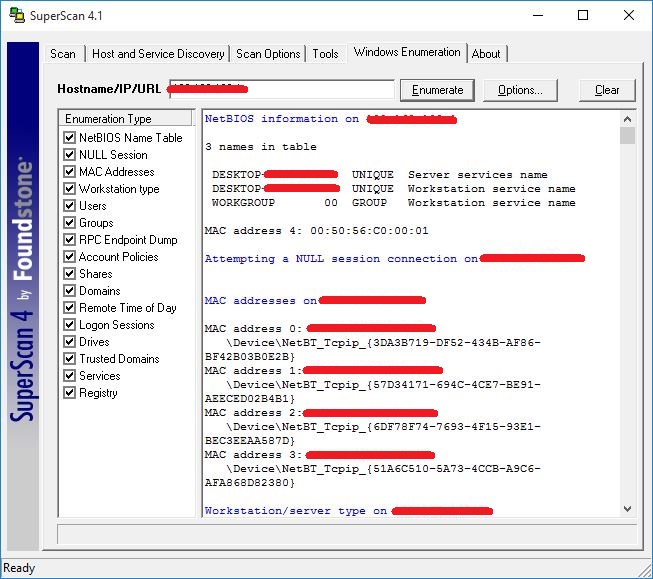
c. Enumerate the identified services to gather more detailed information, such as software versions, running processes, or banners.
5. Conduct operating system (OS) fingerprinting:
a. Use tools like Nmap or P0f (https://lcamtuf.coredump.cx/p0f3/) to analyze network responses and infer the operating system running on target hosts.
b. Gather information about the OS versions and vulnerabilities associated with them.
6. Perform service enumeration:
a. Utilize tools like Nmap or Nessus (https://www.tenable.com/products/nessus) to enumerate services on target hosts.
b. Gather information such as running applications, versions, and configuration details.
7. Document and analyze findings:
a. Record detailed information gathered during the network scanning and enumeration process.
b. Analyze the results to identify potential vulnerabilities, misconfigurations, or weaknesses that could be exploited.