- August 10, 2023
- Posted by: team SOUTECH
- Category: Blog, Cyber-security and Ethical Hacking Training, Ethical Hacking and Kali Linux Free Training, Intelligence, Others, Security, Technologies
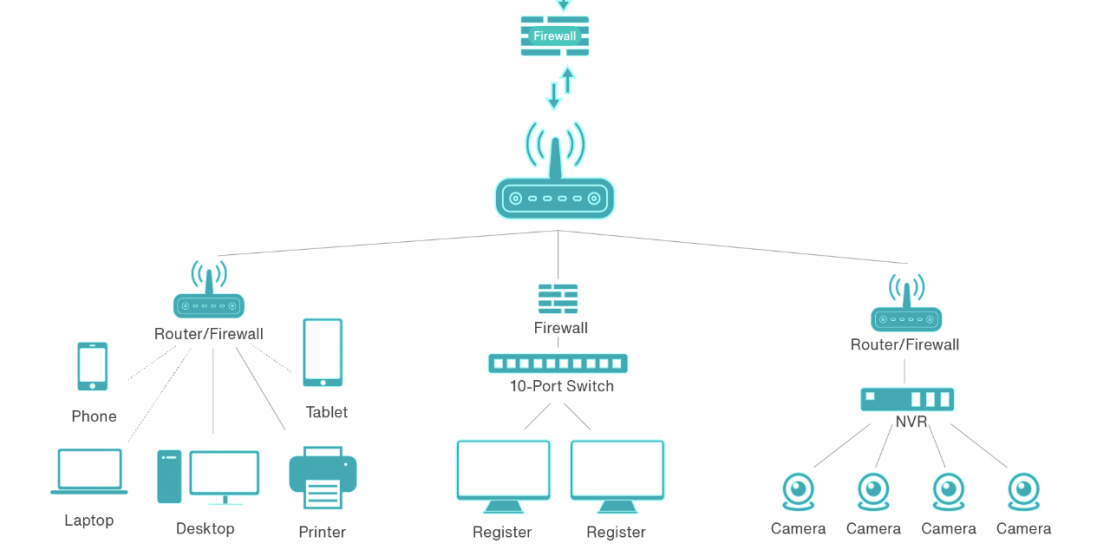
Network segmentation is the practice of dividing a computer network into smaller, isolated segments to enhance security. It helps prevent lateral movement of threats within a network and limits the potential impact of a breach by isolating sensitive assets.
Case Study: A large organization with multiple departments wants to enhance their network security by implementing network segmentation. The IT team assesses the existing network infrastructure and designs a segmentation plan to isolate critical assets and restrict access based on user roles. They configure VLANs on switches and update firewall rules to enforce traffic separation. Regular monitoring and maintenance activities help ensure the continued effectiveness of the network segmentation.
Step-by-step instructions:
1. Assess network infrastructure: Understand the organization’s network architecture, including the number of subnets, network devices, and communication requirements.
2. Identify segmentation requirements:
a. Determine the sensitive data or critical assets that need protection.
b. Identify different user groups and their access needs.
c. Identify regulatory or compliance requirements related to data segregation.
3. Plan the segmentation strategy:
a. Define the segmentation boundaries and scope, such as separating internal networks from external networks.
b. Determine the appropriate network segmentation techniques, such as VLANs (Virtual Local Area Networks) or network zoning.
4. Design network segmentation:
a. Create a logical network diagram that illustrates the planned segmentation layout.
b. Determine the network devices and configurations needed for implementing the segmentation plan, such as routers, switches, and firewalls.
5. Implement network segmentation:
a. Configure VLANs or network zoning on the appropriate network devices.
b. Update firewall rules to control traffic flow between segments.
c. Implement appropriate access controls and security policies for each segment.
6. Test and validate the segmentation:
a. Verify that network traffic is correctly isolated between segments.
b. Test connectivity between devices within the same segment and across segments.
c. Perform security assessments to identify any misconfigurations or vulnerabilities.
7. Monitor and maintain network segmentation:
a. Continuously monitor network traffic and access logs for any unauthorized connections or anomalies.
b. Regularly review and update firewall rules and access control lists (ACLs).
c. Conduct periodic audits and assessments to ensure the effectiveness of the network segmentation.Network segmentation is a critical security measure but requires careful planning, implementation, and ongoing monitoring to achieve the desired level of protection.