- August 7, 2017
- Posted by: cyberanalyst
- Category: Blog, CISSP, Consulting, Cyber-security and Ethical Hacking Training, Development, Others, Outsourcing Link, Project and Research Nigeria, Softwares, Technologies
In my previous articles, I have discussed intensively on vulnerability analysis and penetration testing but I’ll reiterate a few things to help buttress the points in this article.
Penetration plays a major role in the playbook of any security consultant and penetration test and it is the best clue to know how vulnerable a network is to an attack. Compliances such as PCI and HIPAA require vulnerability assessment and they also enable penetration testing to be performed smartly and in a targeted form when compared to performing simple port scans. Vulnerability assessments most importantly is the bedrock for developing an information security program that is proactive, going beyond reactive techniques such as starting firewalls and identifying loopholes and making attempts to seal them. But know this, that when installing and managing your websites and networks even if you might know much about the basic security measures and even follow them, it is never enough to discover and mitigate all the vulnerabilities by yourself.
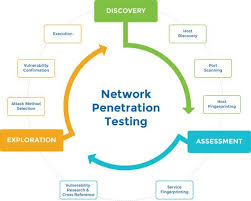
Now lets us understand what a network vulnerability assessment is as an entity of penetration testing. A network penetration testing is a penetration testing technique that involves reviewing and analyzing a network in order to discover any possible security loopholes and vulnerabilities. Network administrators and network security staff use this technique to do a thorough evaluation of their security architecture as well as to defend the computer network against any form of threats and vulnerabilities. It also helps them to assess the network to know its strength. But the key objective of this technique generally is to discover vulnerabilities that may compromise the overall privacy, security and operations of a computer network.
| Want to start an eBusiness and Grow it Globally with free IT, Legal, Internet Discounts,3 Months SME Startup Course, ePayment Integration, Biz Development Services, Free Website, Free SMS Units/Portal all done for you within 30 Days?
Start Here>> Click >>> Start a Digital Business in Nigeria
Network penetration testing Methodology
1. Data and Information gathering and project set up
This involves;
- Reviewing the project to obtain all assumptions
- Listing and detailing out the IP scanned IP addresses
- Configuring the IDS and IPSes to accept the originating IP addresses
- An optional scan of all user credentials
- Obtaining contact information for both parties
- Planning the scans and including the time it is being performed
2. Scanning the tools being setup
This step involves configuring all the vulnerability scanning tools for “safemode”
3. Performing the vulnerability scan
This involves performing and in-depth scan of all provided IP addresses and identifying any security weaknesses and vulnerabilities on user credentials after they have been scanned.
4. Research and Verification of vulnerabilities
This involves
- Verifying all the discovered vulnerabilities
- Identifying false positives
- Determining any potential impacts of the vulnerabilities being exploited
- Prioritizing remediation efforts
- Developing specific plans and recommendations for the remediation
5. Create reports and a project close-out
This involves;
- Delivering final and concluding reports
- Teleconferencing of the scheduled project conclusions
- Ensuring a full understanding of the remediation actions being recommended
- Facilitating knowledge transfer in and effective form
Network Vulnerability Assessment Tools
In order to carry out an automates security audit in any organization, vulnerability scanners play a very critical role. This is because they can scan the website, network and other internal systems for thousands of security risks and can automatically prioritize them alongside the right patches. Some can automatically perform the patches.
Scanning websites is an entirely different ballgame from network scans. In the case of websites, the scope of the scan ranges from Layer 2 to 7, considering the intrusiveness of the latest vulnerabilities. The correct approach for scanning websites starts from Web-level access, right up to scanning all back-end components such as databases. While most Web security scanners are automated, there could be a need for manual scripting, based on the situation.
1.OpenVas: This is a short for Open Vulnerability Assessment System and is a free network security tool that has most if its components licensed under GNU General Public License (GNL). This tools is very effective in scanning for thousands of vulnerabilities and supports concurrent and scheduled scans and tasks. Its main component is available as Linux packages and as virtual appliances that are downloadable for the purpose of testing and evaluation. OpenVas does not work on windows but it offers clients for windows platforms. It can run mainly on Linux platforms and can perform scans and receive over 33,000 updates daily of Network vulnerability tests.
OpenVas has a manager that controls its intelligence and it is command line based with full services of daemon for user management and feed management. It is not easy and quick to be installed but it has one of the richest features in It security scan.
2. Retina CS Community: This is a vulnerability scanning and patching tool for Microsoft and most third-party applications like Firefox, adobe etc. It can scan for vulnerabilities in mobile devices, virtualized applications, servers, web applications, and private clouds as well. It identifies missing patches and configuration issues. It has a software that which is called Retina Network Community which is to be installed first before actually installing the Retina Cs Community software. It works on windows server 2008 or later versions, Microsoft SQL 2008 version or its later versions and it also requires a .net framework 3.5 to be installed, it is IIS server enabled.
It gives you the option of choosing from a variety of scans with reporting templates which can specify IP address ranges. You could also provide any necessary credentials for scanned assets which may be required may make your reports come out in a readily and organized format including email alerts. Most businesses however may find its system requirements very stringent since it requires windows server.
3. Microsoft Baseline Security Analyzer (MBSA): This is a tool that can perform both local and remote scans on windows servers and desktop. These tools are very efficient because it can identify missing service packs, security patches and any common security misconfiguration. Platforms that support it are windows XP Windows 8 and 8.1, windows Server 2012 and windows server 2012 R2. It is an easy-to-understand tool and a straightforward tool as well. It provides options of selecting a single window machine to perform a scan where you can choose a name, specify IP addresses and even choose a domain. You could choose the platform you want to scan which can either be a Windows, IIS, SQL admin vulnerability, windows update or weak passwords.
5. SecureCheq: This is a tool that can perform local scans on both windows desktops and servers and is capable of identifying many insecure advanced windows settings such as COBIT, ISO, CIS standards. It deals majorly on common configuration errors which are related to OS hardening, communication security, data protection issues, audit logs and user account activities. Its free version can only perform less than 24 scans which is about a quarter of what its full version scans. SecureCheq is a simple tool which lists all the checked settings including passed or failed results. Even though it is easy to use and its ability to scan for advanced configuration settings, it cannot reach deep to scan general windows vulnerabilities and network based threats. But it however complements MBSA well enough by scanning for basic threats and performing a follow up scan using securecheq.
6. Qualys freeScan: This tool can perform about 10 free scans of URLs and IPs of local servers and machines on the internet. It can be downloaded from web portals which can be installed and run on virtual machines for scanning internal networks. It can scan for issues in SSL, and vulnerabilities in their related networks.
It may seem first see an online tool which appears to do scan via internet if you put in the local IP address, it prompts you to download to your system via virtual machines like VMware or VirtualBox image. This tool allows you to scan local networks and gives an interactive report of the threats and patches.
7. Wireshark: Wireshark, previously called Ethereal, is one of the most popularly used tools for network vulnerability testing or assessment. This is because it gives you a clear picture of happenings on your network. It works in promiscuous mode in order to capture all the traffic on a TCP broadcast domain. It has features of customized filters that can be configured to intercept specific traffic such as communication between two IP addresses, UDP-based DNS queries on that network.
Data obtained can be dumped into a capture file for later review. It can also look for stray IP addresses, unnecessary packet drops spoofed data packets and any suspicious single IP address. Although wireshark gives one a clearer and broader picture of the network activities, it however does not have its own intelligence and should therefore be used as a data provider.
8. Nmap: This has remained one of the most popular scanning tools for over a decade now. It has the capability of crafting data packets and perform scanning to a TCP granular level such as ACK, SYN scans etc. some of the characteristic of this tool include
- Algorithms for built-in signatures designed to guess OSes and its versions based on the TCP handshake
- It can detect remote devices on the network as well as firewalls, routers, and their models
- It can check for open and running ports and which ports can be exploited for simulation of attacks
- It gives results in plain text and verbose
- It is scripted to automate routine task and obtain evidence for audit reports
9. Metasploit: Metasploit is a tool that comes to play after scanning and sniffing have been done. It provides the following capabilities;
- It is a rigorous tool for performing scans against a set of IP addresses.
- It can be used for anti-forensics
- Programmers can write codes that can be used to exploit vulnerabilities and to test it on Metasploit if its working
- It is a commercially available tool for performing virus attacks.
10. Aircrack: This is a network scanning tool that acts as a sniffer, packet crafter and decoder. It targets a wireless network by subjecting a packet traffic to capture vital information about a certain underlying encryption. A Decryptor is then used to perform a brute-force on the captured file to find passwords. Aircrack can be found in kali-linux which is the most preferable.
11. Nikto: This is an interactive open source tool for scanning websites because it supports HTTPS and HTTP. Nikto works by
- Crawling a website like a human would do in a little amount of time
- It uses a technique known as mutation to create combinations of various HTTP tests to perform an attack.
- It finds critical loopholes like improper cookie handlings, XXL errors, upload misconfigurations etc.
- It dumps all the findings in a verbose mode which can also help in knowing more about vulnerabilities in a website.
Care should be applied when interpreting Nikto logs because it can result in too many things getting noticed and can trigger a false alarm.
12. Samurai framework: It is used to for deep-diving after a baseline check has been done by Nikto. It is a powerful scanning utility which can be used to target specific set of vulnerabilities. It is pure penetration testing tool which focuses on other penetration tools such as WebScarab for HTTP mapping.
13. SQLmap: This tool is a first-generation tool capable of exploiting SQL injection errors but it can as well take over the database server. It works for speedy fingerprinting of the database to find underlying OSes and file system to fetch data from the server.
Note that a regular scheduled network vulnerability scan can help an organization to identify loopholes and weaknesses in a network even before any cybercriminal can perform a seeming attack. The aim of performing a network vulnerability is to identify devices on your network without compromising the systems on your network. Therefore, ensure to conduct a periodic network vulnerability scan on your network in order to discover and mitigate and possible weaknesses on you network before it can be exploited.
Why do you need the services of a Network Penetration Tester?
A network penetration tester is specially and specifically with trained the expertise to effectively conduct penetration testing and network assessments. Note that is a penetration is improperly conducted, it could be detrimental to your organization and its daily operations. Some of the skills a Network security specializes in are;
- Data breach prevention
- Application security
- Security control testing
- Gap analysis maintenance
- Compliance testing and analysis
Who do you contact?
To get a range of services ranging from certifications and trainings in vulnerability and penetration testing and many more courses. We at Soutech web consults have a team of professionals that cannot only train you and your staff on vulnerability and penetration testing which is an entity of cyber security but also conduct them. Endeavour to visit us at soutech web consults or subscribe to our website to find out we can help your organization and your business mitigate any form network vulnerabilities by just implementing any of our test processes and technologies.
| Want to start an eBusiness and Grow it Globally with free IT, Legal, Internet Discounts,3 Months SME Startup Course, ePayment Integration, Biz Development Services, Free Website, Free SMS Units/Portal all done for you within 30 Days?
Start Here>> Click >>> Start a Digital Business in Nigeria