- August 7, 2017
- Posted by: cyberanalyst
- Category: Blog, Business Negotiation, CISSP, Consulting, Cyber-security and Ethical Hacking Training, Development, Digital Marketing, Others, Project and Research Nigeria, Sales and Marketing, Softwares, Technologies
First of all, let us understand what a vulnerability is. I’ll define a vulnerability as any form of loophole, a weakness or mistake that can be found in a system security design, its implementation, security procedures, or its control that can lead to systems security policy violation. A vulnerability can make it possible for cybercriminal or attacker to gain unauthorized access to the system.
As we already know, confidentiality, integrity and availability which are the three cores of IT security. Once any or all of these elements are compromised, then one can say there is a security vulnerability. Infact, a single security vulnerability has the potential of compromising one or all of these elements. For example, the confidentiality can be compromised if there is an information disclosure vulnerability while the compromise of integrity and availability can be as a result of remote code execution.
| Want to start an eBusiness and Grow it Globally with free IT, Legal, Internet Discounts,3 Months SME Startup Course, ePayment Integration, Biz Development Services, Free Website, Free SMS Units/Portal all done for you within 30 Days?
Start Here>> Click >>> Start a Digital Business in Nigeria
What is Vulnerability Testing?
It can also be referred to as vulnerability assessment which is a software testing technique that is conducted in order to evaluate the inherent risk in an IT system and measures employed to reduce or curb the probability of the event.

Vulnerability testing has some similarities with risk assessment and these assessments can be performed following some steps as highlighted below.
- Developing a catalogue for assets and resources in the system.
- Assigning rank orders to quantify resources by value and importance.
- Identifying the potential threats and vulnerabilities to the resources.
- Eliminating totally or mitigating the high ranked vulnerabilities for the most valuable resources.
Vulnerability testing depends majorly on 2 mechanisms
- Vulnerability assessment
- Penetration testing
Objectives of Vulnerability Testing
The common goals and objectives of risk and vulnerability assessments are as follows;

- To get an accurate inventory of all data and IT assets.
- To prioritize organizational IT and data assets according to the importance and criticality to the organization
- To identify and document all the potential risks, threats and vulnerabilities to the organizational infrastructural assets.
- To prioritize the potential risks, threats and known vulnerabilities based on their impact or criticality on the IT or data assets being affected.
- To identify and minimize the vulnerability window of the organizational IT and data assets according to the minimum acceptable tolerance level.
- To curb, mitigate or remediate the identified risks, threats and vulnerabilities and properly plan and budget them based on the criticality of the IT and data assets.
- To check for compliance with the updated information security laws, regulations, procedures and mandates
- Just as explained previously, it helps to identify lapses, voids and gaps in the organizations IT security framework and architecture by looking out for specific recommendations.
- To identify the potential risks, threats and vulnerabilities that an organization’s is susceptible to and to find ways to justify the cost of all the security countermeasures and solutions to be adopted in order to mitigate, eliminate or reduce the identified risks, threats and vulnerabilities.
- To provide an objective assessment and prompt recommendation to help define the organizations goals and objectives for performing risk and vulnerability assessment.
- It helps organizations to understand the return on investments (ROI) whenever funds are to be invested in the IT security infrastructure.
- To scan operating systems, application softwares and the entire network for known vulnerabilities such as insecure authentications and software designs.
Scope of Vulnerability Testing
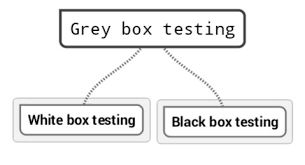
- Black Box Testing: It involves performing vulnerability testing from an external network with no prior knowledge of the internal network infrastructure and systems.
- White box testing: It involves performing vulnerability testing within an internal network with prior knowledge of the internal network infrastructure and systems. White box testing can also be referred to as internal testing.
- Grey box testing: It involves performing vulnerability testing from either an external or internal network with little knowledge of the internal network infrastructure and system. It involves the combination of black box ad white box testing.
Elements of Vulnerability Testing
- Information Gathering: This can also be referred to as reconnaissance and it deals with obtaining as much information as possible about an IT environment. Information such as Networks, IP addresses, versions of operating systems in use etc. and it is applicable to the 3 scopes of vulnerability assessment.
- Detection of vulnerability: This process involves the use of vulnerability scanners to scan the IT environment to identify the unknown and potential vulnerabilities.
- Information analysis and planning: It involves the analysis of all the vulnerabilities that have been identified and further devising a means to penetrate into the network and the systems.
Types of Vulnerability Test
- Predefined Tests: These is a vulnerability test that is designed to discover some common vulnerabilities in databases and its environments. Predefined tests can be customized to suit the needs or requirements of an organization. Predefined tests include;
- Configuration Tests: It checks a database for all configuration settings realted ti security. It looks out for common flaws and mistakes in database configurations. Such configuration issues include;
- Privelege which include; system level rights, privilege access to database and users, rights of use and creation of objects
- Configuration: Which include parameter settings for the database and parameter settings for the system level.
- Authentication: It includes, use of accounts by users, use of remote logins, password policies.
- Version: This includes, versions of the database and patches for the database.
- Object: It involves sample databases that have been installed, database layouts that have been recommended and ownership of the databases.
- Behavioral Tests: This test type checks and analyses the security posture and wellbeing of the database environment. It does this by observing the database when it is in real time mode and checking how information is manipulated. Some of the behavioral tests include;
- Violations of access rules
- Failures in excessive logins
- Errors in the excessive SQL
- Access to default users
- Logins at after hours
- Execution of DDL, DBCC commands from the client side of the database
- Calls for stored procedure checks
- Ensures user ids are not accessed from multiple IP addresses
- Query- based vulnerability tests: This test type can either be a pre-defined test or a user-defined test that can be created easily and quickly by modifying SQL queries which can be run against database entities or resources.
- CVE (Common Vulnerabilities and Exposures) Tests: This test type monitors and exposes common vulnerabilities from the MITRE corporation and further adds the results of the test for related vulnerabilities that are related to the database.
- CAS-based Tests: This test type can either be a predefined test or a user-defined test which is based on the template of a CAS item found in the OS script command. It uses the collected data. Users can therefore check which of the template items and tests against the contents in the CAS results.
Vulnerability Testing Methodologies
- Setup:
- Begin the documentation process of all assets
- Secure permissions to credentials and assets
- Perform tools update
- Configure the tools
- Execute the Test
- Run the tools to begin execution
- Run all the data packets captured (A packet is a unit of data that is crafted to be routed from a source to destination). If a file whether email, HTML, or URL request is being sent from a particular point to another on the internet, the TCP layer of TCP/IP will divide the file into small chunks each having a sequence number on the headers for efficient routing. Now, these small individual chunks are referred to as packets. On the destination end, the packets reassemble to form the original file that was sent while running the assessment tools.
- Analyze the vulnerabilities:
- Define and classify the system resources as well as the network
- Prioritize the resources based on their importance such as High, Medium, low
- Identify all potential threats to the assets
- Based on the priorities, develop a strategy to first handle the most prioritized problems
- Define and implement measures to mitigate or minimize the consequences of the occurrence of an attack.
- Form a Report: Develop a report of all the steps you took to arrive at your results. The report is also important in order to guide to aid future understanding of the system and as well to report to the management of the organization.
- Remediation plans: This process involves developing measures and taking the appropriate steps to fix the vulnerabilities.
Responsibilities of a Vulnerability Tester
- Unit management such as Information Security Coordinators and Unit IT supervisors
- They support and enforce the standards, approve and submit the annual risk assessment documents to management
- They determine the person who maintains the documentation.
- They also request for the internal audits, procure and assign the necessary resources that are needed to implement the standards and polices.
- They notify the users and support staff who are involved in performing the test.
- The also request for any exceptions
- They supervise and coordinate the vulnerability test and also the remediation processes.
- The System administrator and Computing device Administrator
- They implement the best practices which are needed to comply with the test.
- They support and comply with the policies.
- They scan all the systems in the network for compliance to standards devices.
- They monitor the systems actively for any available patches in other to remediate tasks that can affect the user.
- Information security Officer
- These people approve and oversee the all the vulnerability scans.
- They review and approve the use of any alternative scanning tools when required.
- They conduct reviews and risk assessments annually.
- They authorize the removal of network devices from the network when needed.
Vulnerability testing focuses more on determining loopholes and weaknesses in an IT infrastructure. In my next article i will try to shed some more light on the tools which can use to perform vulnerability since we already have the standard methodologies to follow in order to perform a detailed vulnerability test.
Soutech ventures offers courses that can better equip and train you on all you need to know with practical hands-on knowledge on vulnerability assessment. Subscribe to our CEH course today on www.soutechventures.com/courses
| Want to start an eBusiness and Grow it Globally with free IT, Legal, Internet Discounts,3 Months SME Startup Course, ePayment Integration, Biz Development Services, Free Website, Free SMS Units/Portal all done for you within 30 Days?
Start Here>> Click >>> Start a Digital Business in Nigeria

