- July 14, 2017
- Posted by: cyberanalyst
- Category: Cyber-security and Ethical Hacking Training
The WannaCry Decryptor Virus is a virus that was popularly coined from two words wanna and “cry” which came up as worldwide attack using a cryptoworm, targeted at computers that were running the Microsoft Windows Operating System by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency.
The attack was introduced first on 12th May 2017, a Friday precisely and just within a day it was reported to have infected more than 230,000 computers in over 150 countries. Major examples were parts of Britain’s National Health Service (NHS), Spain’s Telefonica, FedEx and Deutsche Bahn were hit. In UK, this virus attack affected about 47 NHS trusts, which lead to operations being cancelled and patients turn away from A&E.
Shortly after the attack began, Marcus Hutchins, a 22-year-old web security researcher and security expert from North Devon in England who blogs as “Malware-Tech”, discovered an effective “kill switch” by registering a domain name he found in the code of the ransomware when he bought a web domain for less than £10. This greatly slowed the spread of the infection, effectively halting the initial outbreak on Monday, 15 May 2017, but new versions have since been detected that lack the kill switch.
| Want to start an eBusiness and Grow it Globally with free IT, Legal, Internet Discounts,3 Months SME Startup Course, ePayment Integration, Biz Development Services, Free Website, Free SMS Units/Portal all done for you within 30 Days?
Start Here>> Click >>> Start a Digital Business in Nigeria
Ever since then, many researchers in different countries have been on their toes to find ways on how to recover data from infected machines under the attack of this virus.
Working Principle
The Wannacry ransomware program locks all the data on an affected computer system and leaves the user with only two files. It carries instructions on what to do next to retrieve the files.
The “WannaCry” ransomware appears to have used a flaw in Microsoft’s software, discovered by the National Security Agency and leaked by hackers, to spread rapidly across networks thereby locking away files.
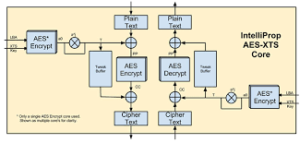
Its method of encryption is the popular AES (Advanced encryption techniques) and RSA (Rivest Shiamir Adleman) encryption ciphers which therefore means that the hacker can directly decrypt the system files using a unique decryption key.
When the software is opened it tells computer users that their files have been encrypted. The cybercriminal then gives their victims a few days to pay up, warning that their files will otherwise be deleted. Payment is demanded in Bitcoins (an online cryptocurrency) with instructions on how to buy it, and provides a Bitcoin address to send it to.
What is Ransomware?
This malware attack involves a hacker taking administrative privileges over a system and blocking access to it until a certain ransom specified by them is paid.

In order for cyber attacker to gain access to the system, there is a certain type of malicious software which they need to download and then load on a device within the network to execute it. The victim is then lured to click and download the link he is sent.
Immediately this software gets onto the victim’s computer, the cybercriminal can then launch an attack which locks all files it can find within the network. Files are encrypted gradually, one after another.
Large organizations that have the most sophisticated security systems may be able to spot any anomaly on their network and take measures to minimize the damage by isolating documents
Most computer security companies have ransomware decryption tools that can bypass the software.
How to protect yourself against a Ransomware attack
I will list down some steps that can best protect you against this virus
- Have all files backed up in a completely separate system. When you do this, you won’t suffer any loss of document once you’re attacked.
- The most common ways of installing the virus are through compromised emails and websites. Therefore, always endeavor not that are not secure that can be susceptible to cross-site attacks and SQL injections. Launching this attack can take a difficult process to carry out but a lot of patience is always required.
- One of the best ways to protect yourself is to be suspicious of unsolicited emails and always try to type out web addresses by yourself rather than clicking on links. Another key defense strategy to install antivirus programs that can scan files before they are downloaded, as well as block secret installations and look for malware that may already be on a computer.
- Hackers need to download the malicious software onto a computer, phone or other connected device. Example, a hacker can send an employee a phishing email that looks like it comes from their boss asking them to click open the link. Such links however redirect you to a malicious website that surreptitiously downloads the virus onto their computer. Therefore, downloading a corrupted program or application and visiting a website that is displaying malicious adverts can also lead to infection of a device.
What is the way out?
Cyber security companies have developed sophisticated defenses against this cyberattack, including machines that fight back when they spot hackers in a system.

What to do if you’re a victim – should you pay the ransom?
Victims are advised never to pay the ransom as it encourages the attackers. In a couple of occasions, there is no surety that when you pay the ransom, your files will be released and intact. Instead, the best thing to do is restore all files from a back-up. If this isn’t possible, there are some tools that can decrypt and recover some information.
How much do hackers demand, and why in Bitcoin?
The victim is often required to pay amounts between 0.3 and 1 Bitcoins which is about £400 to £1,375. A payment in dollars may be also required in denominations of the bitcoin.
The digital currency is popular among cybercriminals because it is decentralized, unregulated and practically impossible to trace. You can do a little more study of the Bitcoin.
Although it may seem like a small amount to charge, the ransomware attacks are often widely distributed, so the ransom payments can stack up.
To get daily updates on major cybersecurity attacks, subscribe to our page. Soutech web consultants is a IT firm that provides quality options to protection from all kinds of viral challenges on your network or system. Get in touch with us today for your internet solutions.
| Want to start an eBusiness and Grow it Globally with free IT, Legal, Internet Discounts,3 Months SME Startup Course, ePayment Integration, Biz Development Services, Free Website, Free SMS Units/Portal all done for you within 30 Days?
Start Here>> Click >>> Start a Digital Business in Nigeria