- August 7, 2017
- Posted by: cyberanalyst
- Category: CISSP, Cyber-security and Ethical Hacking Training, Mobile Application Development Service and Training, Others, Softwares, Technologies, Website Design Service Abuja, Website Design Training, Website Hosting
Polymorphic viruses have over the years been one of the most difficult and complex viruses to detect. Anti-virus manufacturing companies have had to spend days and months trying to create detection routines required to track a single polymorphic.
I’ll attempt to discuss about polymorphics and some of the detection mechanisms existing and also introducing Symantec’s striker Technology, a patent-pending mechanism for detection of polymorphics.
The Norton anti-virus 2.0 was the maiden version to include a striker for possible detection of polymorphics.
| Want to start an eBusiness and Grow it Globally with free IT, Legal, Internet Discounts,3 Months SME Startup Course, ePayment Integration, Biz Development Services, Free Website, Free SMS Units/Portal all done for you within 30 Days?
Start Here>> Click >>> Start a Digital Business in Nigeria
The Evolution of Polymorphic viruses
A computer virus can be defined as a self-replicating computer program that functions without the permission of the user. In order to spread, it attaches a copy of itself to some part of the program such as a word processor or a spreadsheet. A virus can also attack boot records and master boot records that contain all the information that a computer needs to startup.
Some viruses can replicate themselves, some may display messages input by its creator, some can be designed to deliver a part of a payload to corrupt programs, delete files, reformat a hard-disk drive, shutdown or crash a corporate network. I will quickly discuss about some viruses before we can relate it to polymorphic viruses.
Simple Virus
All a simple virus does is to replicate itself such that if a user launches the program, the virus gains control of the computer and attaches a copy of itself to other program files. After it spreads successfully, the virus transfers control back to the host program, which functions normally. You can perform a simple anti-virus scan to detect this kind of infections.
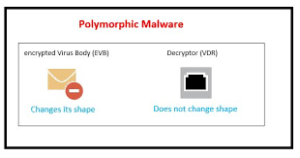
Encrypted Virus
The mode of operation of the encrypted virus was via signatures. Its idea was to hide the fixed signatures by scrambling the virus therefore making it unrecognizable by the virus scanner.
An encrypted virus is made up of a virus decryption routine as well as an encrypted virus body such that if the user launches the infected program, the virus decryption routine first gains control of the computer, then decrypts the body of the virus.
Polymorphic viruses
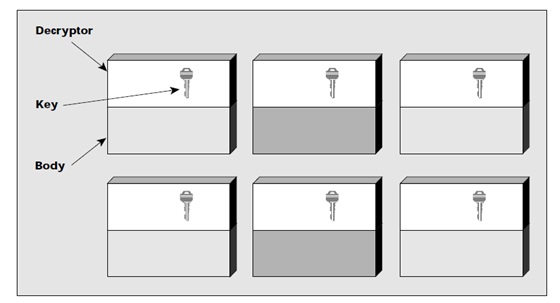
The polymorphic virus is built in such a way that it has a scrambled virus body and a decryption routine that first gains control and then decrypts the virus’ body. However, it possesses a third component which is a mutation engine that sort of generates randomized decryption routines which change each time the virus infects a new program.
The mutation engine and the virus body are both encrypted such that when a user runs a program infected with a polymorphic virus, the decryption routine first gains control of the computer, then decrypts both the virus body and the mutation engine.
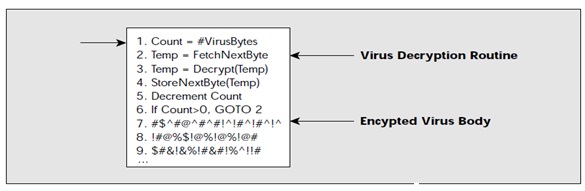
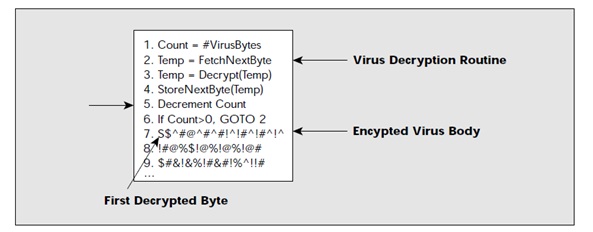
The decryption routine then transfers control of the computer to the virus, which locates a new program to infect. At this point, the virus makes a copy of both itself and the mutation engine in random access memory (RAM). The next thing the virus does is that it invokes the mutation engine, which will randomly generate a new decryption routine that will decrypt the virus and yet does not bear any resemblance to the previous decryption routine. The virus encrypts the new copy of the virus’ body and the mutation engine. Finally, the virus then attaches this new decryption routine, alongside the newly encrypted virus and mutation engine to the new program.
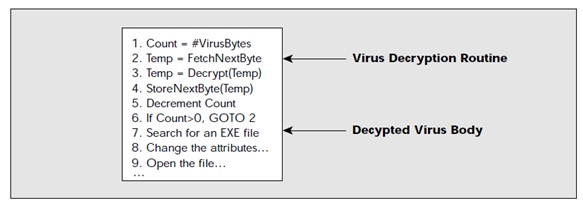
So, we can see that not only is the virus’ body encrypted, but the decryption routine varies from infection to infection. This therefore confounds a virus scanner searching for the tell-tale sequence of bytes that identifies
a specific decryption routine. With a signature that is not fixed to scan for, and a non-fixed decryption routine as well, no two infections look alike.
Detecting a Polymorphic Virus
Anti-virus researchers launched an attempt to fight back by developing special detection routines crafted to detect and catch each and every polymorphic virus. Special programs were written by line for line which were designed to detect various sequences of computer codes known to be used by all the mutation engines to decrypt the virus body.
This approach was not feasible, it was as well time consuming and costly. Every new polymorphic virus needs its own detection program and also, a mutation engine which produces seemingly random programs which can properly execute decryption and some mutation engines to generate billions of variations.
Moreover, a lot of polymorphics make use of the same mutation engine, credits to the authors of viruses like dark avenger. In addition to this, different engines are being used by different polymorphics to generate a similar decryption routine, which can make identification of the virus solely based on decryption routines wholly unreliable.
This approach can be misleading by identifying one polymorphic as another. These shortcomings led anti-virus researchers to develop generic decryption techniques that trick a polymorphic virus into decrypting and revealing itself.
To gain more knowledge about all forms of malwares with malware analytical skills subscribe to our CEH course at Soutech Ventures. We have trained and seasoned experts to give you both theoretical and hands-on ethical hacking knowledge and skills.
| Want to start an eBusiness and Grow it Globally with free IT, Legal, Internet Discounts,3 Months SME Startup Course, ePayment Integration, Biz Development Services, Free Website, Free SMS Units/Portal all done for you within 30 Days?
Start Here>> Click >>> Start a Digital Business in Nigeria