- August 7, 2017
- Posted by: cyberanalyst
- Category: Blog, CISSP, Consulting, Cyber-security and Ethical Hacking Training, Others, Softwares, Technologies, Website Design Training
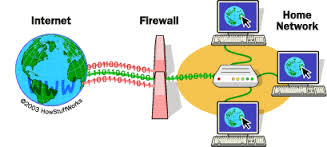
A firewall just as its name implies is a protective barrier whose function is more like a physical firewall. The firewall lies just between the computer and the connection it has with the internet to provide protection from any form of online threats.
A firewall is a software program or a piece of hardware device that is programmed to provide security for your computer by placing limitations on information that you can receive from an external network. A firewall is designed to either allow or block information coming in or out of a network based on certain security policies.
The term firewall came into the cybersecurity world as a borrowed term from the word firefighting where an effort is made to prevent the spread of fire.
Organizations actually started moving from the use of mainframe computers and dumb clients in a client-server model and therefore the need to put a control over the server became a top priority. Before the introduction of firewalls in the late 80’s, the only form of protection from the outside world was the use of Access control lists (ACLs) resident in routers. The function of the ACLs was to choose which IP address to grant or deny access to a certain network.
| Want to start an eBusiness and Grow it Globally with free IT, Legal, Internet Discounts,3 Months SME Startup Course, ePayment Integration, Biz Development Services, Free Website, Free SMS Units/Portal all done for you within 30 Days?
Start Here>> Click >>> Start a Digital Business in Nigeria
Due to the swift growth of the internet and increased rate of connectivity of people and organizations to networks, it gradually meant an end of the ACL as a filtering method which was not enough to keep of malicious traffic. This was so because basic about network traffic was embedded in the packet header. The first organization to deploy the use of firewalls to tackle the threat of cyberattacks was the Digital equipment Corp (DEC) in 1992.
Types of Firewall Techniques
- Packet Filter Firewalls: This type of firewall handles the packets going in or out of the network based on pre-defined rules by the user.
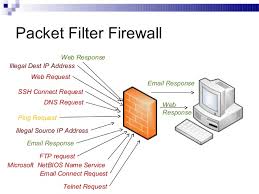 The packet filtering ability is fairly transparent and effective to users however can be difficult to configure. It is however very susceptible to IP spoofing.
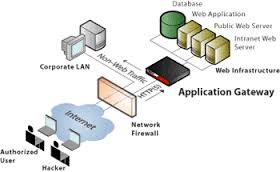
The packet filtering ability is fairly transparent and effective to users however can be difficult to configure. It is however very susceptible to IP spoofing. - Application gateway Firewalls: This type of firewall applies security configurations to specific applications like the Telnet and FTP servers. The application gateway firewall is very effective but can impose some performance degradations.
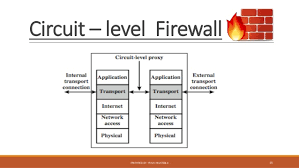
- Circuit-level Gateway firewalls: This firewall type applies its security configurations when a TCP or UDP connection has been established. Therefore, once this connection is established, the packets begin to flow between the hosts without any further verification.
- Proxy Server Firewalls: This firewall type intercepts all the messages that go in and out of the network. The proxy server firewall cascades or hides the real network address of the host.
The benefits of a firewall
- It prevents any unauthorized user from an external network from gaining access to your internal network i.e. your computer in your network.
- It monitors all forms communications that goes on between your computer and other computers outside of you network and over the internet.
- It establishes a protective shield that either allows or blocks any attempt to access data or information on your computer.
- It sends out a warning when any other computer tries to connect to you.
- It also warns against any illegitimate connection by an application on your computer that gives access to other computers.
The Limitations of a Firewall
Firewalls however have not been able to determine the contents of email messages that are sent to your computer so they cannot you from malware sent through phished emails.
So therefore:
- The need for antivirus softwares that can detect, quarantine or delete suspicious email attachments
- Learn to protect yourself from phishing scams
If you have a private network, ensure that you protect your devices by configuring the firewall settings on your computers and wireless router. You can also add an extra level of security to your personal computers by using security softwares. However, even if your wireless network may seem secure, it may not be secure from other types of malware that can be gotten from computers through the internet.
Build your firewalls such that it can defend you against hackers and viruses. You can do this by always ensuring that your firewall is turned on. You can configure the firewall settings in the security and privacy section which can be found under your systems preferences section.
Also ensure to do regular updates of your anti-virus software as an extra security measure. Please note that firewalls and anti-viruses are not the same thing
Finally, asides the protection a firewall offers you, learn safe online practices.
If you need to learn about firewall configurations, and purchase latest and licensed anti-virus softwares contact us at soutech ventures. Subscribe to us today for all types of IT trainings and consultations you may require.
| Want to start an eBusiness and Grow it Globally with free IT, Legal, Internet Discounts,3 Months SME Startup Course, ePayment Integration, Biz Development Services, Free Website, Free SMS Units/Portal all done for you within 30 Days?
Start Here>> Click >>> Start a Digital Business in Nigeria