- July 29, 2017
- Posted by: cyberanalyst
- Category: Blog, CISSP, Consulting, Cyber-security and Ethical Hacking Training, Softwares, Technologies

Think of espionage with characters like James Bond, whereby you have to disguise yourself and to travel halfway around the world, infiltrating organizations to grab sensitive information. Although the James Bond character is just a fictional representation, such methods of spying however are becoming quite extinct. With the advancement of digitized data, we’re swiftly shifting towards the version of cyber-spying.
Espionage in recent times depicts the spying process entirely. Since Organisations and institutions store almost all their data on systems, cyber spies just stay on the confines of their computer desk and trot around in an attempt to hack into those systems.
Cyber espionage has over the years been a criminal case where authorities have to prosecute users to avoid them installing antivirus softwares and other security measures on their computer systems.
What is Cyber Espionage?
It is also called Cyber Spying and it is the act of using the internet to obtain sensitive secrets and information of an individual, a rival, competitor, a group or government for personal, political and economic advantages.
A few Trends in Cyber Espionage
As revealed in Volume 20 of Symantecs Internet security Threat Report (ISTR), Regin and Turla were two highly versatile forms of malware that were being used in espionage.
Till date, Regin is one of the most sophisticated pieces of malware which has the characteristics of a chameleon by providing attackers with tools like screen captures, remote access, deleted file recovery network snooping, and stealing as well.
On the hand, Turla works in a way that attackers use watering-hole tactics and spear-phishing to launch attacks on the embassies of former Eastern Bloc countries and governments as well.
Attackers have remote access to infected computers via Turla by helping them steal files, connect to servers, delete files and hosting spywares online.
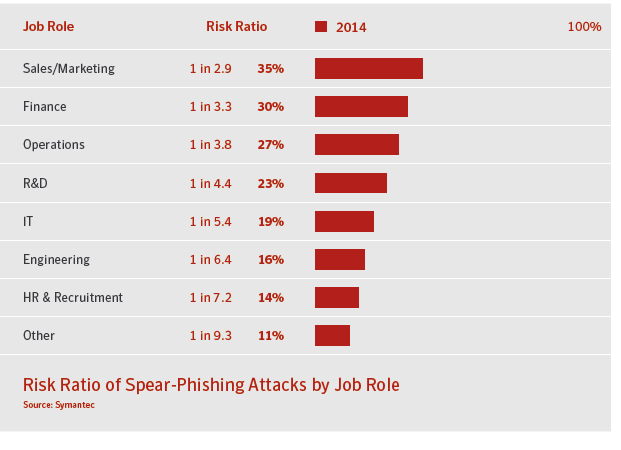
Spear-phishing increased by 8% in the year 2014 and it came in form of spams with a few number of high-volume recipients because few individuals were targeted. As a result of these findings, the need to educate employees within organizations on best practices as regards internet usage has increased.
Who performs cyber Espionage?
Equation group and Hidden Lynx were the few prominent attack groups that were being highlighted by ISTR. And in addition to these attack groups, there are entities called the state actors which are acting on the behalf of government bodies, hacktivists, patriotic hackers, data thieves and scammers etc. are all involved in cyber espionage. While some attackers are after stealing of business intellectual property, others are after sensitive data belonging to government and some going as far as launching attacks on energy grids, industrial systems and petroleum pipelines.
How Cyber Espionage is Performed
The process of carrying out cyber espionage is often a very complex process and does not just involve dumping some malware on a target system, it involves a more sophisticated process whereby the chose their targets and the type of information they’re aiming to steal and look forward to cause some level of damage.
Infiltration is not just the process where the attacker tries to exploit some zero day software vulnerability in the quest to gain access to an organizations network but he tries to find a software vulnerability within the network of an organization and also the network of individuals working in the organization. An attack of this sort sometimes requires some human factor of social engineering like phishing campaigns in order to succeed.
As you may know already, when an attacker wants to target a person, they will try to go online and carry out some reconnaissance on them, they look for social media sites, blogs or anything that will give them some extra information on their victim’s interests. They often use any information gathered to narrow their phishing campaigns towards areas that may be attention-catching to their targets. Once they have succeeded in getting their attention, they can go ahead to lure them into opening the emails, clicking on the malicious links or downloading some malicious software onto their system.
If the victim is able to complete that particular task, the malware will be installed on the computer of the victim thereby giving the attacker access to the network where they can perform their intended mission of espionage.
How to keep your organization and Information safe from Cyber espionage
- Protect your Passwords: Always protect your passwords because it is a very handy weapon in the hands of a cybercriminal. If a cybercriminal gets a hold of your password, username and email address, they can use specially crafted tools to crack your password. The use of Two-factor authentications when available are also advised. You can read more on password protection.
- Be on the watch for any forms of phishing attacks. Educate yourself on the downsides of phishing. And always try to identify spoofed emails. Read more on phishing.
- Learn more about software security. Always perform software updates on a regular basis once there are any available updates. Softwares are usually patched of loopholes- the reason updated versions. So, leaving your programs or softwares outdated can create room for loopholes which an attacker can harness.
- Protect your social media accounts: Like I said earlier, attackers often do research on their targets before making any attempts to attack so always ensure to that the privacy settings of your social media accounts are in check. Always prevent any personally information from public view and be wary of people you do not know trying to be contact with you.
- Bring Your Own Device (BYOD):Always ensure that you put in place some kind of device control mechanism that will protect you against data leakage. This will not only allow certain external devices but it will also encrypt your data. When data is used later on a different system inside the company’s environment, the 7mdash standard automatically decrypts it and makes it usable but when loaded on a system without a device control mechanism, it will become automatically useless.
- Ensure that a device control mechanism is put in place such that it can safeguard your system against data leakage. Not only can it only allow certain (USB) devices to be inserted, it will also encrypt the data. When the data is later used on another system inside the company’s environment, the data will automatically be decrypted 7mdash; and thus usable — but when copied to a system that does not have the Device Control Mechanism installed, it will be useless.
There has been no concrete manual on how to ensure protection from targeted attacks of intellectual property. In environments where this type of attack is small-scaled, it can appear completely undetected. Staying security-educated via security vendors’ websites such as soutech ventures keeps you appraised with new threats and how to protect yourself. You can be well educated on how to keep your intellectual property from cyber espionage.