- August 13, 2017
- Posted by: cyberanalyst
- Category: Blog, CISSP, Consulting, Cyber-security and Ethical Hacking Training, Development, Mobile Application Development Service and Training, Others, Project and Research Nigeria, Softwares, Technologies

Having Wi-Fi readily available in public places has become a trend in larger cities of the world. Public places such as restaurants, coffee shops, libraries, hotel rooms, auxiliary offices, airports and other places you can think of have all adopted the use of Wi-Fi. Having a free and easily accessible internet connection to use can be a very convenient way of catching up with your work, meeting targets, accessing your online accounts, checking your mails etc. However, we seem not to know to the security risks associated with the use of publicly available Wi-Fi’s. Well, like you know already that one of best ways to optimally and speedily access your sensitive information and carryout sensitive transactions through Wi-Fi, there are some measures you need to take additionally in order to kept safe online which is the purpose of this write up.
According to a popular research journal published by Norton, said that over 68% people fell victim to publicly available and unsecured Wi-Fi’s in the last year. Therefore, we must take practical measures and efforts to make sure our devices are kept safe and protected.
Brief History in the encryption standard adopted by the Wi-Fi
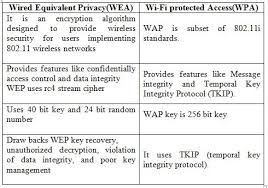
Let me shade some more light on the encryption protocols and standards that existed before the encryption protocol adopted for use by Wi-Fi’s. One of the security problems faced by older encryption standards is in the aspect of security which was adopted by some wireless networks. One of the first encryption schemes for wireless network devices was the Wireless Encryption Protocol (WEP) and this encryption standard was found to be weak and very easy to crack. Although the WEP protocol is still regularly found as an option in many wireless access points and devices, there is need to give way for upgrading hardware that will be supported by newer standards whenever it is possible.

WEP was developed with the intention to manage the following;
- To prevent eavesdropping in communications which aims at reducing any forms of unauthorized disclosure of data.
- To ensure data integrity while it flows across the network.
- Encryption of packets during transmission using a shared secret key.
- To allow access control, confidentiality and integrity in a lightweight and efficient system.
However, WEP failed in handling some of these issues which birth WPA.
The Wireless Protected Access (WPA) came as a successor to WEP and was birth with the intention of checking and curbing the many issues faced by the WEP standard. This is the reason why its encryption abilities addressed some vulnerabilities however it was being found vulnerable and cracked. It was designed not to required full hardware upgrades as compared to the WEP.
However, its processing power and mechanisms were being limited especially where older versions of hardwares were involved. The TKIP standard was one of the standards developed to platform the WPA. TKIP was an improved standard for the WEP protocol because at every point there is a static and unchanging key being used for every frame transmitted.
WPA however suffered from the following flaws;
- Weak key selection by users
- Issues of packet spoofing
- Issues with authentication as regards Microsoft Challenge Handshake.
This gave way to the WPA2 standard intended to address the flaws in WPA. WPA came with a stronger and tough encryption standard which are CCMP (Counter Mode with Cipher Block Chaining Message Authentication Code Protocol) and AES (Advanced Encryption Standard). It also employs the TKIP Temporary Key Integrity Protocol and MIC (Message Integrity Code) as encryption standards.
This enterprise is a version that incorporates the EAP standard as a medium to improve the strength of the security and also make the system scalable for use in large organisations and enterprises. WPA2 is special because it offers an improved security when compared over its predecessors and maintains the IEEE 802.11i standard for security. It uses a server to carry out its key management and authentication for its wireless clients.
The WEP, WPA and WPA2 all suffer serious vulnerability issues which an attacker can exploit in order to take advantage of the victim. All of them offer ways to be exploited in recent times.
Why Public Wi-Fi is Vulnerable to cyber attacks
Given all the risk associated with all the protocols described above, users still suffer a great deal from unknown and known flaws. The fact that you may need a password to log in to access the Wi-Fi does not mean that your activities online are encrypted and that a publicly available Wi-Fi is secure. There a few issues that make public Wi-Fi’s susceptible to attacks and one of the issues related to the encryption protocol which the Wi-Fi technology adopts. Another issue has to do with the possibility of connecting to a rogue Wi-Fi hotspot. Tools like Aircrack-ng have been built and are readily available online to perform brute force attacks on any weak passwords and keys involving WEP and WPA.

The risk of joining a rogue Wi-Fi hotspot is also a big issue when using free public Wi-Fi’s. All a hacker has to do is to create a rogue hotspot with the intention of unleashing a sort of Man-in-the-middle (MITM) attack on whoever becomes a victim by connecting to the rogue Wi-Fi. When this attack occurs, it allows a hacker to intercept the communication that goes on between you and the server of the website you are visiting at a time. There are pre-built tools that can be used to easily eavesdrop, capture sensitive information like login credentials, credit card numbers and social media security passwords etc. and monitor online traffic for performing MITM attacks
What are the signs that you may have logged on to a Rogue Wi-Fi?
Of course, you know that once a device discovers a Wi-Fi network it probes the known networks which an attacker can leverage on. An attacker can configure a rouge Wi-Fi hotspot which can look like a typical home network that can be found in a coffee shop. Therefore, your device can be connected to the hackers’ rogue Wi-Fi hotspot instead of connecting to the real publicly available Wi-Fi hotspot.
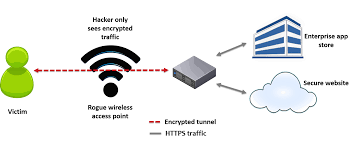
Another trick you should know is that, a public Wi-Fi network can be created with the name Free Wi-Fi which is flooded for victims to be connected to them and very naturally people will want to join such networks especially if the free internet service is offered. I must say I personally has been a victim to this a few years ago. If you are at a coffee shop, or at home or in a public place and suddenly your device shows you have been connected to your home network, there are huge chances that someone has been able to grab your devices’ or computers broadcast request. If also you are browsing a website or webpage such as your bank or favorite social media page that should normally be HTTPS instead it shows HTTP, then you must know that someone might have connected to your network. Once this person has linked up to your network, the person can perform a MITM attack by serving you a HTTP version of the site with the intention of capturing your login credentials. So, you must always be on the lookout these little details.
What are the Measures you can take to ensure your safety on a Public Wi-Fi?

- Accessing Sensitive information using public Wi-Fi: I will as a matter of fact always advice anyone never to use public Wi-Fi’s to access their sensitive information. If there is need at any point in time to access your sensitive data online, you need to switch you’re your local ISP or get someone to pretty much share their device hotspot with you. You can do use the public Wi-Fi to browse for things like directions and other things that are less sensitive like getting information from google, bing or yahoo. If you’re trying to process things like paying of bills or even shop online, these things can wait. If it is an urgent situation which you need to achieve, the use of a VPN (Virtual Private Network) is advised. There is a plethora of trusted VPNs online and obviously if you need a good service, then you need to pay for such VPNs. Ensure you choose a reputable VPN security provider.
- Use VPNs (Virtual Private Network): If there is a need to use a publicly available Wi-Fi to do your work and your company or organisation offers a VPN access, ensure to make use of it. VPNs provide a private tunnel for you to transmit or communicate by adding an extra layer of security for your connection.
- Visit HTTPS only: If you are using a public Wi-Fi, ensure to avoid websites that are HTTP (not protected or secure) and visit or browse websites that begin with HTTPS.

Why am I saying so, if you are an IT expert, you not, you must know that HTTPS are encrypted and provide an extra layer of security which makes browsing more secure. If you connect to an HTTP site which is unsecure, a hacker can easily see your traffic if he snoops around the network.

- Consider installing an extension such as HTTPS-Everywhere in order to re-route all the websites you visit to HTTPS. There is a tool offered by the Electronic Fronteir Foundation which provides this option.
2.Configure wireless settings on your device: Configure your device not to connect automatically to any available Wi-Fi hotspots. This can be done by navigating to the wireless settings of your PC or device. This setting makes sure your device does not automatically and unknowingly gets connected to any public network. On your PC, just turn off the “connect automatically” option. When you do this, you prevent your device from broadcasting to the world that it is attempting to get connected to the “home network” which a hacker can easily spoof.
- Use Privacy screens: Hackers are everywhere and are usually not afraid of using any means possible to access and obtain your data, you must consider making use of privacy screens if there is a need to access sensitive information in a public place.
In general terms, whether or not you are using a your smart-devices or PC’s to access some sensitive information like accessing your bank account and financial information, always ensure not to do it in a publicly available Wi-Fi network. Ensure to consider all the tips above to keep your information protected online.
Soutech ventures offers a comprehensive information security course such as (CEH and CISSP) which can give more security insights, tools/tips and countermeasures in the different facets of technology. Subscribe to our services today.
Cybersecurity and Ethical Hacking- Kali Linux Training in Abuja,Nigeria