- March 16, 2018
- Posted by: SouTech Team
- Category: Others, PHP Programming and Development, Softwares, Technologies
Bcrypt is a powerful hashing algorithm which when deployed via configurable number of rounds is scalable with the hardware. During the process of using bcrypt hashing method, Its slowness and rapid multiple rounds make it impossible for attacker to exploit since it needs and requires massive funds and hardware to be able to crack the passwords set using bcrypt.
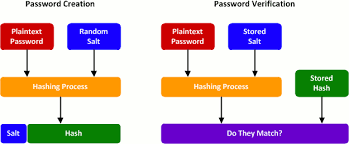
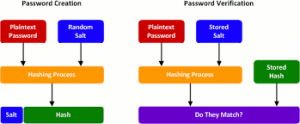
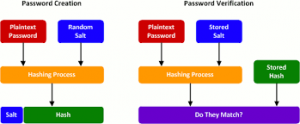
In hashing, a salt is a random data which is used to add additional input to the function that “hashes” data, a password or even passphrase. Salts are like the concept of nonce since they are closely related.
As you can see now that without ludicrous amount of funds and hardware, Attack on hashed password using bcrypt method is virtually unfeasible and unachievable.
What algorithm did bcrypt uses: What is an algorithm -> A programming algorithm is the computer procedure which tells the computer precisely the required steps to take when solving a problem or reaching a goal. Algorithms can be likened to the way we cook at home in the sense that recipe is the “procedure”, ingredients are the “inputs” while the results are the “outputs”
Bcrypt hashing method uses an algorithm called “EKSBLOWFISH”. Eksblowfish algorithm is a variant of the blowfish cipher, modified to make the setup of hashing to be much expensive and unpredictable as it names implies ‘EKS’ stands for ‘Expensive Key Schedule’. Hello reader, It doesn’t make it significantly cryptographically stronger, but once it is used, It in intended to hinder brute-force attacks and It makes it unsuitable for any application requiring key agility.
I would love to share the little history on the invention of Eksblowfish. It was designed by Niels Provos and David Mazieres for password hashing in OpenBSD. It was invented to make it parameterized in nature (cipher) and it takes the cost parameter in ‘$’ sign that controls how expensive the key scheduling works and also takes into consideration the family key known as ‘SALT’ meaning that both the cost and the salt parameters define the cipher family. On each family, a key determines an encryption function in the usual way because its family can encapsulate an Eksblowfish cipher family.
Eksblowfish and Blowfish are exactly the same in the encryption phase because the key schedule phase of Eksblowfish ensures that any schedule phase of Eksblowfish ensures that any subsequent state depends on both salt and key (user password), and no state can be precomputed without the knowledge of both blowfish and Eksblowfish. Since it needs to check for key difference, bcrypt is regarded as ONE-WAY HASHING ALGORITHM
What is one-way hashing algorithm: It means that the user cannot retrieve the plain text password without already knowing the salt, rounds and key which is the password. A one-way hash function makes it possible for us to build digital signatures which in turn identify the sender and the message of the digital distributed message.
How to use bcrypt
Password hashing functions was fully built into PHP 5.5 or greater since it is now the integral part of any database storing container. You are to use password_hash() to create the bcrypt hash of any password entered by the user when choosing password.
HASHING PASSWORD USING password_hash()
<?php
$my_password=”Godisgreat@$0_23851”;
$hashed_password=password_hash($my_password,PASSWORD_DEFAULT);
echo $hashed_password;
echo ‘<br>’
// $2y$10$cWgdMT/Kw5llS5ybVDO00ezd5XCeRcWrD6K6ecPfguUPnsesGqkCS
?>
RETRIEVING PASSWORD USING password_verify()
<?php
$hashed_password=”$2y$10$cWgdMT/Kw5llS5ybVDO00ezd5XCeRcWrD6K6ecPfguUPnsesGqkCS”;
If(password_verify(‘Godisgreat@$0_23851’,$hashed_password)){
echo “Password Matches”;
}
else {
echo “Password Mismatch”;
}
?>
Aftet practicing all the examples, So, you want to use bcrypt? Awesome! You must never do it yourself. I know that you will be worry about many things like managing keys, or storing salts or generating random numbers yourself and using logic to verify it, You are making a big mistake because you are doing it wrong. The reason is as simple as reciting alphabets: It is so easy and straightforward to screw up bcrypt. My adive again is that never make any formulated bcrypt yourself because you can’t let it wrk professionally.
It is better to leave it for the experts who has a broad expertise on creating and maintaining it.
Instead, You can use available libraries in the store based on the requirements that you want to meet. Few of the libraries are :
- PHP 5.5 API
- ZEND/BCRYPT/PASSWORD/CRYPT
- PASSWORDLIB
- PHPASS
Many different choices are made available and the choice to choose is up to you
Do you want to see all these libraries in action and build a secure web application using PHP. People who are passionate about building and developing programs and applications for the world must put into consideration how to secure the password of the users and you are looking towards building and learning how to enhance, maintain and build secure web application.
See some of the details you will learn at our PHP Class: Click Below
Learn PHP Programming in Nigeria Today
Take Action TODAY!