Others
-
cybersecurity-room
March 14, 2024 -
The Data Analyst’s Playbook: Winning Strategies for Analytical Excellence
February 21, 2024 -
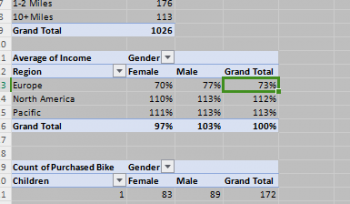
Beyond Pie Charts: Crafting Visually Stunning Narratives with Data
February 21, 2024 -
Data Alchemist’s Handbook: Turning Information into Strategic Gold
February 21, 2024 -
The Data Explorer’s Guide: Charting Unknown Territories with Analysis
February 21, 2024 -
Data Analysis Zen: Finding Serenity in the Sea of Information
February 21, 2024 -
Crunching Numbers with Impact: The Essentials of Data Analysis
February 21, 2024 -
Data Intelligence: Elevating Your Business IQ through Analysis
February 21, 2024 -
Deciphering the Data Code: A Guide to Effective Analysis Strategies
February 21, 2024 -
Data Analysis Revolution: Shaping Tomorrow’s Business Landscape
February 21, 2024 -
The Agile Data Analyst: Adapting Strategies for Dynamic Insights
February 15, 2024 -
Data Symphony Orchestra: Achieving Perfect Harmony in Analysis
February 15, 2024 -
Free Cisco Information Technology Essentials Training Course
November 9, 2023 -
nyscacademy
November 1, 2023 -
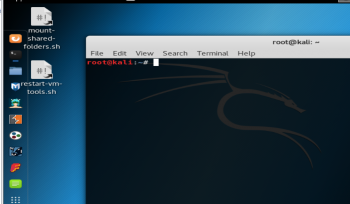
Step by step guide on how to implement Kali Linux as host OS on a PC: Tutorial
October 2, 2023 -
datathon2023
September 11, 2023 -
Risk Management in PMP: A Comprehensive Guide
September 5, 2023 -
5 Things You Should Know Before Installing Solar Panels
September 2, 2023 -
How to become a data analyst: Guide to Technical and Non Technical Skills
September 2, 2023 -
Step by step guide on product design part 2
August 13, 2023 -
Step by step guide on product design part 1
August 13, 2023 -
“Game On: Elevating Sports Excellence through Data Science and Analytics”
August 10, 2023 -
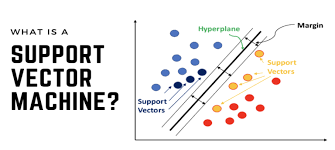
Sculpting Intelligence: Mastering Support Vector Machines for Supervised Learning Excellence
August 10, 2023 -
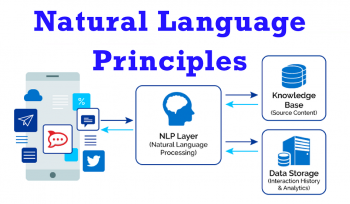
Lexicon Alchemy: Transforming Language into Intelligence with Natural Language Processing (NLP)
August 10, 2023 -
Ethics Unveiled: Navigating Data Privacy and Responsibility in the Age of Innovation
August 10, 2023 -
Artificial Intelligence in Healthcare: Revolutionizing Patient Care and Diagnosiss
August 10, 2023 -
Cybersecurity Web Application Attacks: A Case Study of SQL Injection Attack
August 10, 2023 -
Incident Response Planning: Developing an Incident Response Plan
August 10, 2023 -
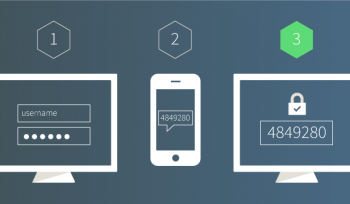
Authentication Methods: Implementing Two-Factor Authentication (2FA)
August 10, 2023 -
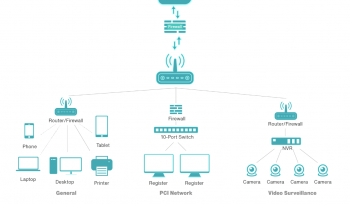
Network Segmentation: Implementing Network Segmentation for Enhanced Security
August 10, 2023 -
SO YOU WANT TO BE A DATA ANALYST
May 6, 2022 -
CISCO CyberOps lab – Create User Accounts; cybersecurity training
July 26, 2021 -
CSS Selectors, Typography, Color Modes, and More
July 16, 2021 -
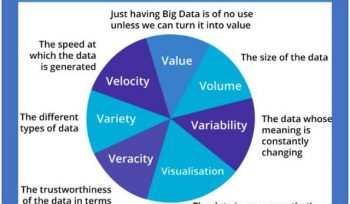
7 V’s of Big Data: IoT(Internet of Things) and Big Data
May 4, 2021 -
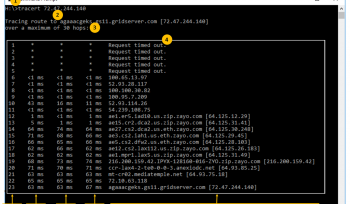
Gathering information using Windows Command Line Utilities
February 25, 2021 -
How to Install an SSL Certificate on your Website
February 25, 2021 -
CCNA: Switching, Routing, and Wireless Essentials
February 23, 2021 -
Introduction to IoT
February 23, 2021 -
CCNA Security
February 23, 2021 -
CyberOps Associate
February 23, 2021 -
Cybersecurity Essentials
February 23, 2021 -
Introduction to Cybersecurity
February 23, 2021 -
Networking Essentials
February 23, 2021 -
Massive Discount on all our Trainings
January 11, 2021 -
5 ways to optimize your content quickly
January 7, 2021 -
Reasons Why You Should Use Solar Power
January 5, 2021 -
Demystifying the Solar System Set Up Process for Beginners and Professionals
December 12, 2020 -
Guide to Lead Generation
November 7, 2020