- August 7, 2017
- Posted by: cyberanalyst
- Category: Others
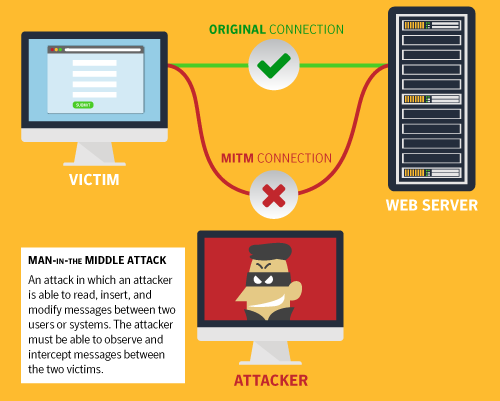
I will simply describe a man-in-the-middle attack as eavesdropping. In this form of attack an attacker intercepts or gets in-between the transmission of data from a computer A(Client) to a computer B (Server/website). They can then inject tools that are programmed to listen-in on the transmissions with the aim of capturing valuable information. In many occasions, the data are modified in transmission in order to trick the user to give out sensitive information such as their log in credentials. Of course, if the user becomes a victim of this attack, his original data will be forwarded unaltered to the attackers preferred destination.
How Man-In-The-Middle attacks work
This attack comes in two forms
- The form that involves being within the physical proximity of the target.
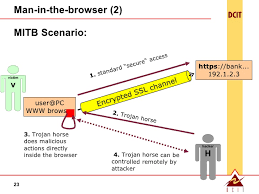
- The form that involves the injection of a malware which is also known as a man-in-the-browser (MITB) attack.
In a traditional MITM attack, an attacker will have to gain access to a Wi-Fi router that is not unsecured. You will often find this kind of connections in public areas with free Wi-Fi hotspot and even in home’s. All the hacker tries to do is to scan the router in search of any weaknesses in configuration and poor use of passwords in the router. Immediately the hacker finds a loophole, they will proceed to injecting their tools to sniff the user and computer visits.
The man-in-the-browser attack is a newer variant of the man-in-the-middle attack and has gained a lot of popularity with cybercriminals because of its ease of execution. Here, the attacker needs a means to inject the malware into a computer after which it installs itself in the users’ browser without their knowledge. Data such as financial institutions is then recorded and sent between specified target site and the victim. The malware transmits the data back to the attackers’ system once it has collected the specific data it was programmed to collect.
A very good example of these type of attack was in recent discovery of the POODLE bug, to know more about the POODLE bug read here. This bug allowed the attackers to capture transmitted data between browsers such as login credentials for e-commerce, and other financial types of online accounts targeted to allow them have control of those accounts.
Another example was the attack on the 3rd of March 2015 by researchers called FREAK which worked such that it allows an attacker to sniff encrypted traffic flowing from a visitor to a website and the website in form of a MITB attack. To know more about the freak attack read here.
The vulnerability was a result of the old encryption standards developed in the 90s which was neglected when out in the custody of Google and Apple. Hackers were able to easily decrypt messages using the old code.
How to avoid this form of attacks.
Here are a few practical steps you can take to reduce the risk of the man-in-the-middle and man-the-browser attacks.
- Always look out for any potential phishing emails from attackers. Read more on phishing. To learn more about phishing, please take out to time to read through my article on phishing. This phishing attacks come in the form of asking you to click a certain link that is provided which demands that you update your password and other log in credentials. Instead of clicking those links, just take some time to type the URL of the website provided on your browser and access it from there.
- Ensure that “HTTPS” is always in the URL bar of any website you’re visiting.
- Avoid as much as possible direct connection to any public Wi-Fi routers. IF you need to connect, you can use a Virtual Private Network (VPN), you could also use a browser plug-in like HTTPS Everywhere (link) or ForceTLS (link).
- Ensure that your private network is always secured. Endeavor also to change any default usernames and passwords on your home router an any other internet device.
- Finally, MITB attacks primarily make use of malware for execution therefore you should update your system with a detailed internet security solution (anti-virus).
To learn more about Man-In-The-Middle attacks, subscribe to our very detailed and comprehensive course modules in Certified Ethical Hacking (CEH). In Soutech Ventures, we have certified tutors to guide through our course contents. visit our website today to enroll. www.soutechventures.com