- September 7, 2017
- Posted by: cyberanalyst
- Category: Blog, CEH, CISSP, Consulting, Cyber-security and Ethical Hacking Training, Development, Digital Marketing, Others, Project and Research Nigeria, Technologies
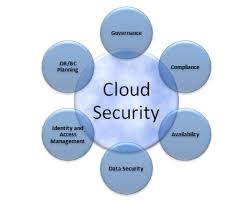
One of the major issues that Computer Information Officers and chief Information Security Officers (CISO) is in the aspect of gaining visibility into the posture of their cloud security. How can they be expected to put in the place the proper and necessary controls and security measures if they cannot even identify where there are security flaws and where they exist.
If there isn’t a new approach, the problems will aggravate even before there is any hope of rendering a solution. Now why is this so?
Let us see various ways;
Without a new approach, the problems promise to get a whole lot worse before they get better. Why? Let us count the ways:
1.Growth of public cloud: Organizations have now deployed the use of cloud services to a much degree ever more than before. According to a study the use of cloud services in the average enterprise now amounts to about 1,427 services.
2. Shadow IT:

A lot of the publicly available cloud services and applications result from the initiative of the shadow IT are usually out of the control of the security teams and line-of-business managers why seem not to be familiar with security and best practices in compliances.
3. DevOps: Like I mentioned in my follow-up article on DevOps, DevOps teams have continued to outpace security teams going out on their own to deploy public cloud services to increase the rate of their development.
 These teams do not often want to dragged behind by the concerns of the security and compliance.
These teams do not often want to dragged behind by the concerns of the security and compliance.
4. Tools and technologies that have become extinct: Traditional tools that can be used for monitoring remediation endpoints have not been effective in the environments of data centers and cannot be effective and efficient for use in the security of public clouds.
5. The Pace of change: For manual processes to be able to keep to the pace, cloud environments change too quickly. Let us assume that organizations are even able to hire and retain personnel that are trained and have experience in the compliance and management of cloud security. CISOs and CIOS need to really worry about complacency in the use of cloud storage because public cloud providers like amazon web services and MS Azure have stepped up their game in the past couple of years. And because of this, surveys have shown that IT heads are becoming less worried of the security challenges in cloud environment. It has also been discovered that the biggest risks are always more in the internal network than in the external network.
6. The relationship between automation, visibility and continuous security and compliance: The questions therefore is on how CIO’s and CISOs gain the needed visibility they may need in order to minimize and maximize protection. The simple answer is through automation and this can be achieved by automating the process of remediation, analyzing and putting up monitoring measures across the whole cloud environment, security teams can gain the visibility they need in order to address their biggest cloud security and compliance challenges. The architecture of the cloud makes it a perfect fit for an automated approach to security and compliance this is because architecture of the cloud environment uses the API model, cloud-native agentless solutions. This architecture can be deployed to give IT security and DevOps teams some level of tremendous visibility and flexibility. With and automated model, it is very possible for CIO and CISOs can;
- Obtain a view that gives bigger picture across all their cloud environments with a centralized means to manage and control events.
- Allow DevOps and other teams to manage best practices in security and compliance that can be necessary for their own cloud deployments and controls.
- Lower costs and reduce risk levels and complexities which can be done by replacing manual tasks with processes that are automated.
- Enhance time with respect to value which can be achieved by securely making use of the public cloud to empower the smaller teams be they individual lines if businesses or DevOps
- Flag risks and remediate the threats even before they get an opportunity or chance to affect availability, compliance and operations.
Finally, a plethora of openings Public cloud services have created for security officers by helping them to deliver significant value to their establishments in a lower costs, accelerated development cycles and greater work rate in productivity. However, there are a lot of risks masked behind these opportunities and these risks are surrounded by security and compliance. But the good thing is that there is a success path which can result in automation for providing continuous security and continuous compliance. This is the time to take the first step towards cloud security.
To learn more about the security of the cloud environment as well as other security methodologies such as, vulnerability assessments, risk assessments and penetration testing, subscribe to our services at soutech ventures to learn CEH course in details.


