SOUTECH Ventures > Articles by: SouTech Team
SouTech Team
-
Google Cloud Digital Leader Training and Certification
October 1, 2024 -
Google Cloud Digital Leader Certification: Overview
September 23, 2024 -
How to Get Started with a Career in DevOps: A Complete Guide
September 12, 2024 -
Want to Know About DevSecOps: DevSecOps and its Importance
September 12, 2024 -
Free Skill Aquisitions
June 14, 2024 -
Guide on how to Purchase Domain name and Hosting from SOUTECHHosting.com -Website Design Tutorial
May 19, 2024 -
cybersecurity-room
March 14, 2024 -
cybermeetup
March 12, 2024 -
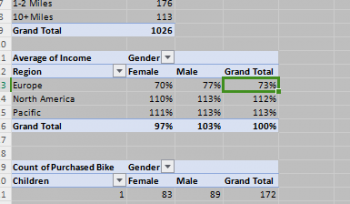
The Data Analyst’s Playbook: Winning Strategies for Analytical Excellence
February 21, 2024 -
Beyond Pie Charts: Crafting Visually Stunning Narratives with Data
February 21, 2024 -
Data Alchemist’s Handbook: Turning Information into Strategic Gold
February 21, 2024 -
The Data Explorer’s Guide: Charting Unknown Territories with Analysis
February 21, 2024 -
Data Analysis Zen: Finding Serenity in the Sea of Information
February 21, 2024 -
Crunching Numbers with Impact: The Essentials of Data Analysis
February 21, 2024 -
Data Intelligence: Elevating Your Business IQ through Analysis
February 21, 2024 -
Deciphering the Data Code: A Guide to Effective Analysis Strategies
February 21, 2024 -
Data Analysis Revolution: Shaping Tomorrow’s Business Landscape
February 21, 2024 -
The Agile Data Analyst: Adapting Strategies for Dynamic Insights
February 15, 2024 -
Data Symphony Orchestra: Achieving Perfect Harmony in Analysis
February 15, 2024 -
Using Sales Funnel and AIDA model to automate your marketing and have 300% ROI for your business
December 9, 2023 -
Important aspects of CSS into case studies with sample code snippets for each
December 8, 2023 -
cybersecurity resources
December 7, 2023 -
cybersecurity Internship
November 24, 2023 -
Free Cisco Information Technology Essentials Training Course
November 9, 2023 -
Data Visualization with Tableau- Step by Step Guide- Tutorial 01
November 5, 2023 -
nyscacademy
November 1, 2023 -
scholarship
November 1, 2023 -
Step by step guide on how to implement Kali Linux as host OS on a PC: Tutorial
October 2, 2023 -
How to install Kali Linux in VMware on a Mac computer: Step by step guide
October 2, 2023 -
How to install Kali Linux in Oracle VirtualBox on a Windows computer: Step by Step Guide
October 2, 2023 -
How to install Kali Linux in VMware on a Windows computer: Step by Step Guide
October 2, 2023 -
Step-by-Step Guide to Secure Your WhatsApp Account with OTP and Two-Step Verification
September 17, 2023 -
Mastering Figma Shortcuts: Boost Your Design Workflow with These 50 Tips
September 15, 2023 -
Mastering Social Engineering: A Comprehensive Guide for Beginners and Intermediate Analysts
September 13, 2023 -
Wireshark step by step guide for beginners
September 12, 2023 -
20+ Linux Commands and explanation on how to use them – step by step
September 12, 2023 -
datathon2023
September 11, 2023 -
Computer Networking: The Significance of Computer Networking in Modern Tech Careers
September 9, 2023 -
Which Is Best for a DevOps Engineer: Python, PHP, Go, or NodeJS?
September 8, 2023 -
How to Become a Professional DevOps Engineer: A Comprehensive Guide
September 8, 2023 -
A step by step guide on Branding, UI/UX, and Product Design in Nigeria
September 7, 2023 -
Elevating Digital Frontiers: Tailored Solutions in Branding, UI/UX, and Product Design
September 7, 2023 -
A Beginner’s Guide to B.J. Fogg’s Behavior Model in UI/UX Design
September 7, 2023 -
Mobile App Development with Flutter vs React Native- Exploring PHP MySQL Backend
September 4, 2023 -
top 10 project management tools and basic steps on how to use them: a guide
May 25, 2023 -
How to become an expert in R for data science and machine learning – step by step guide
May 15, 2023 -
ethical hacking and digital forensics training
May 13, 2023 -
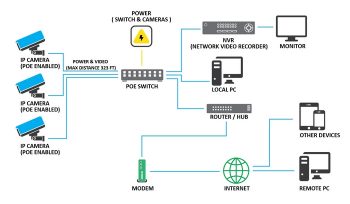
CCTV Installation training and services
April 7, 2022