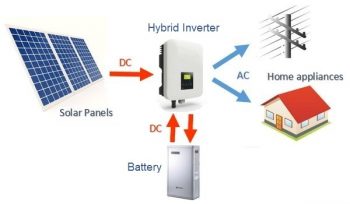
Technologies
-
5 Things You Should Know Before Installing Solar Panels
September 2, 2023 -
Step by step guide on product design part 2
August 13, 2023 -
Step by step guide on product design part 1
August 13, 2023 -
“Game On: Elevating Sports Excellence through Data Science and Analytics”
August 10, 2023 -
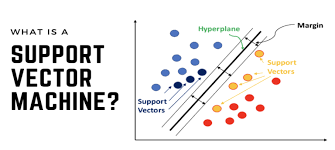
Sculpting Intelligence: Mastering Support Vector Machines for Supervised Learning Excellence
August 10, 2023 -
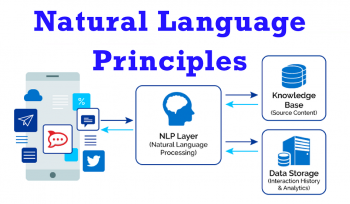
Lexicon Alchemy: Transforming Language into Intelligence with Natural Language Processing (NLP)
August 10, 2023 -
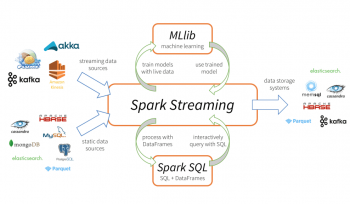
Spark Ignited: Unleashing the Power of Apache Spark for Big Data Revolution
August 10, 2023 -
Ethics Unveiled: Navigating Data Privacy and Responsibility in the Age of Innovation
August 10, 2023 -
Cryptocurrencies and Blockchain: The Future of Finance and Beyond
August 10, 2023 -
Augmented Reality in Education: Immersive Learning for the Future
August 10, 2023 -
Artificial Intelligence in Healthcare: Revolutionizing Patient Care and Diagnosiss
August 10, 2023 -
Ethical Hacking and Penetration Testing: Performing a Web Application Penetration Test
August 10, 2023 -
Cybersecurity Incident Reporting and Documentation: Reporting and Documenting a Security Incident
August 10, 2023 -
Digital Certificates and Certificate Authorities: Obtaining and Verifying a Digital Certificate
August 10, 2023 -
Unveiling the Cyber Frontier: Mastering Network Discovery and Enumeration for Enhanced Cybersecurity
August 10, 2023 -
Cybersecurity Web Application Attacks: A Case Study of SQL Injection Attack
August 10, 2023 -
Incident Response Planning: Developing an Incident Response Plan
August 10, 2023 -
Authentication Methods: Implementing Two-Factor Authentication (2FA)
August 10, 2023 -
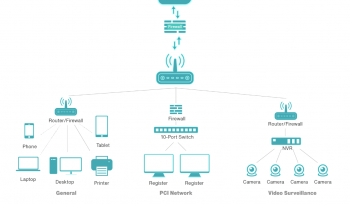
Network Segmentation: Implementing Network Segmentation for Enhanced Security
August 10, 2023 -
CISCO CyberOps lab – Navigating the Linux Filesystem and Permission Settings; cybersecurity training
August 18, 2021 -
CISCO CyberOps lab – Linux Servers; cybersecurity training
August 15, 2021 -
CISCO CyberOps lab – Getting Familiar with the Linux Shell; cybersecurity training
August 15, 2021 -
CISCO CyberOps lab – Reading Server Logs; cybersecurity training
August 7, 2021 -
CISCO CyberOps lab – Attacking a mySQL Database; cybersecurity training
August 5, 2021 -
Certified Information Systems Security Professional (CISSP) – Training in nigeria
May 10, 2021 -
cPanel guide and walk through
February 25, 2021 -
How to Install an SSL Certificate on your Website
February 25, 2021 -
Guide on how to Purchase Domain name and Hosting from Soutech Hosting
February 25, 2021 -
How to Become a Front-end Designer
February 25, 2021 -
Massive Discount on all our Trainings
January 11, 2021 -
With Enpass Password Manager, You Enjoy Super-Strong Passwords That Stay Yours
September 30, 2020 -
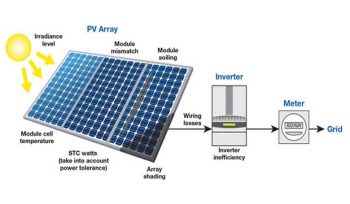
Calculation On How To Design Solar PV System
September 29, 2020 -
Android Users Advised To Delete These 16 Apps That Can Steal Texts And Contacts
September 29, 2020 -
Tools for a Successful Solar System Installation
September 28, 2020 -
How To Maintain Your Solar Battery
September 28, 2020 -
Major Components Of A Solar Power System
September 28, 2020 -
5 Things You Should Know Before Installing Solar Panels
September 26, 2020 -
All You Need To Know About Calculating Solar Panel, Inverter And Battery Charger Specifications
September 26, 2020 -
How to choose the perfect charge controller
September 26, 2020 -
Hackers could use Windows 10 themes to steal passwords
September 9, 2020 -
Google Maps to Add New Feature That Shows Places With Highest COVID-19 Outbreaks and Infection Rates
September 8, 2020 -
How to use Huawei Share to maximise your laptop and smartphone combo
September 7, 2020 -
Human Resource Management
August 20, 2020 -
Ethical Hacking , Data Science, Digital Growth Hack Workshop in Owerri- SOUTECH Hub
November 23, 2019 -
October 2019 Professional IT Training: website design, ethical hacking, digital marketing, data science abuja
October 10, 2019 -
SOUTECH Hub Free Digital Skills Training
October 1, 2019 -
Top 20 Hacking Tools in 2019- Hack Your Way to Cyber Security Protection
September 26, 2019 -
Professional IT Training in Owerri with Amazing Bonuses: Data science/Machine learning, Digital Marketing/Growth Hacking, Cyber Security/Ethical Hacking, Solar and Inverter
September 21, 2019