Softwares
-
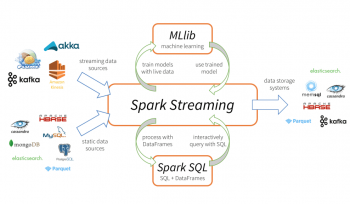
Spark Ignited: Unleashing the Power of Apache Spark for Big Data Revolution
August 10, 2023 -
CISCO CyberOps lab – Convert Data into a Universal Format; cybersecurity training
August 30, 2021 -
CISCO CyberOps lab – Social Engineering; cybersecurity training
August 20, 2021 -
CISCO CyberOps lab – Navigating the Linux Filesystem and Permission Settings; cybersecurity training
August 18, 2021 -
CISCO CyberOps lab – Linux Servers; cybersecurity training
August 15, 2021 -
CISCO CyberOps lab – Getting Familiar with the Linux Shell; cybersecurity training
August 15, 2021 -
CISCO CyberOps lab – Using Windows PowerShell; cybersecurity training
August 12, 2021 -
CISCO CyberOps lab – Investigating an Attack on a Windows Host; cybersecurity training
August 10, 2021 -
CISCO CyberOps lab – Reading Server Logs; cybersecurity training
August 7, 2021 -
CISCO CyberOps lab – Attacking a mySQL Database; cybersecurity training
August 5, 2021 -
CISCO CyberOps lab – Exploring DNS Traffic; cybersecurity training
August 5, 2021 -
CISCO CyberOps lab – Anatomy of Malware; cybersecurity training
August 3, 2021 -
Downloading a Website using Website Copier tool
February 25, 2021 -
How to Install an SSL Certificate on your Website
February 25, 2021 -
Guide on how to Purchase Domain name and Hosting from Soutech Hosting
February 25, 2021 -
Massive Discount on all our Trainings
January 11, 2021 -
With Enpass Password Manager, You Enjoy Super-Strong Passwords That Stay Yours
September 30, 2020 -
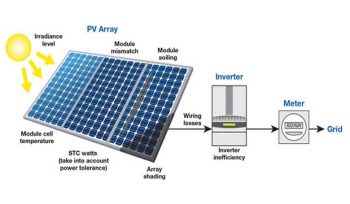
Calculation On How To Design Solar PV System
September 29, 2020 -
Android Users Advised To Delete These 16 Apps That Can Steal Texts And Contacts
September 29, 2020 -
Native Mobile App Development
August 23, 2020 -
Software Testing: Beginner to Advanced
August 21, 2020 -
Human Resource Management
August 20, 2020 -
How to Code in Python – Using Jupyter Notebook Guide
August 14, 2020 -
Ethical Hacking , Data Science, Digital Growth Hack Workshop in Owerri- SOUTECH Hub
November 23, 2019 -
Advanced Encryption Package
October 24, 2019 -
Clearing Logs On Linux
October 24, 2019 -
Hping Commands
October 24, 2019 -
Web Server Security Tool
October 24, 2019 -
Enumeration Using SoftPerfect Network Scanner Tool
October 16, 2019 -
Enumeration Using Super Scan Tool
October 16, 2019 -
How to Install Kali Linux on VMware VM : Cyber Security Training Programs Abuja Nigeria
October 14, 2019 -
Web Server Foot-printing Using ID Server Tool
October 13, 2019 -
Steganography
October 11, 2019 -
October 2019 Professional IT Training: website design, ethical hacking, digital marketing, data science abuja
October 10, 2019 -
Downloading A Website Using A Website Copier Tool
October 5, 2019 -
SOUTECH Hub Free Digital Skills Training
October 1, 2019 -
How to Create a Subdomain on SOUTECH Hosting: Top hosting companies in Nigeria
September 28, 2019 -
Top 20 Hacking Tools in 2019- Hack Your Way to Cyber Security Protection
September 26, 2019 -
Hacking Mobile Platforms: Ethical Hacking Training in Abuja, Lagos, Nigeria
July 22, 2019 -
Career Tips: Ways To Earn Money As A Front-End Developer
June 6, 2019 -
Choose A Framework for Your Next Hybrid Mobile Application Development Project
June 4, 2019 -
Hybrid Application Development: How to Choose the Best Technology Stack.
June 4, 2019 -
How to Migrate My Localhost Database to Online Server
October 17, 2018 -
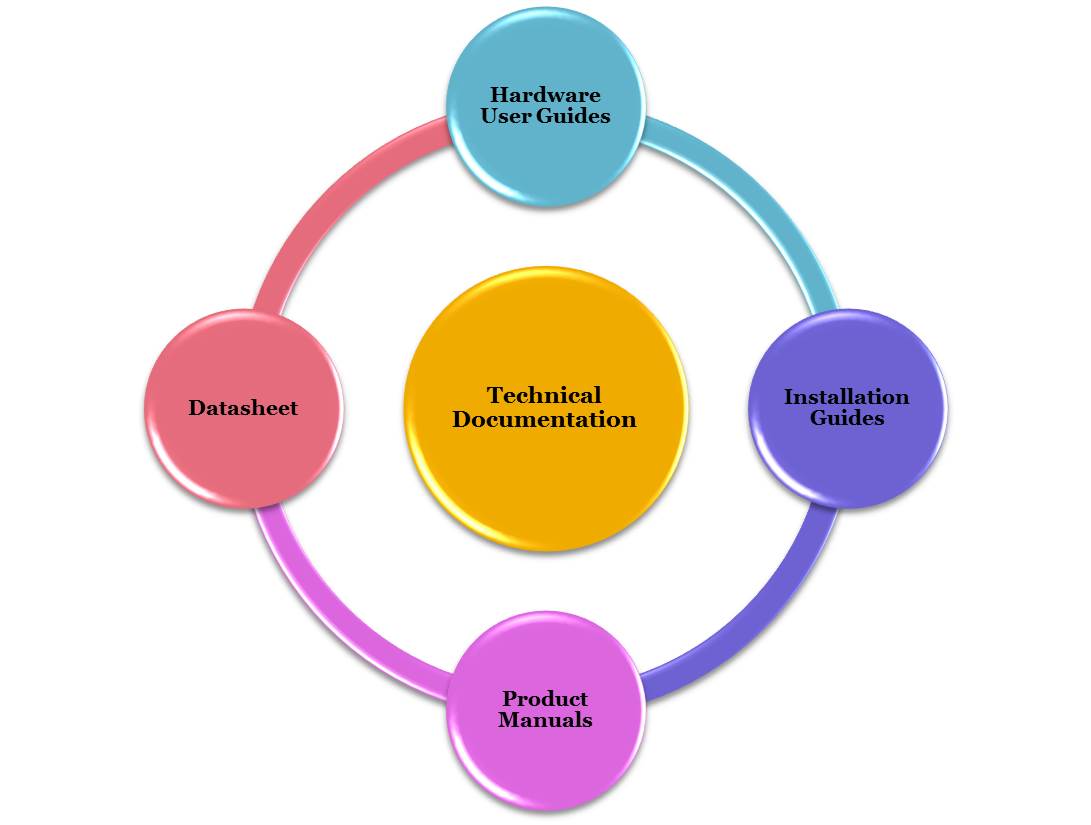
How Do I Prepare Technical Documentation of a Website Application
September 11, 2018 -
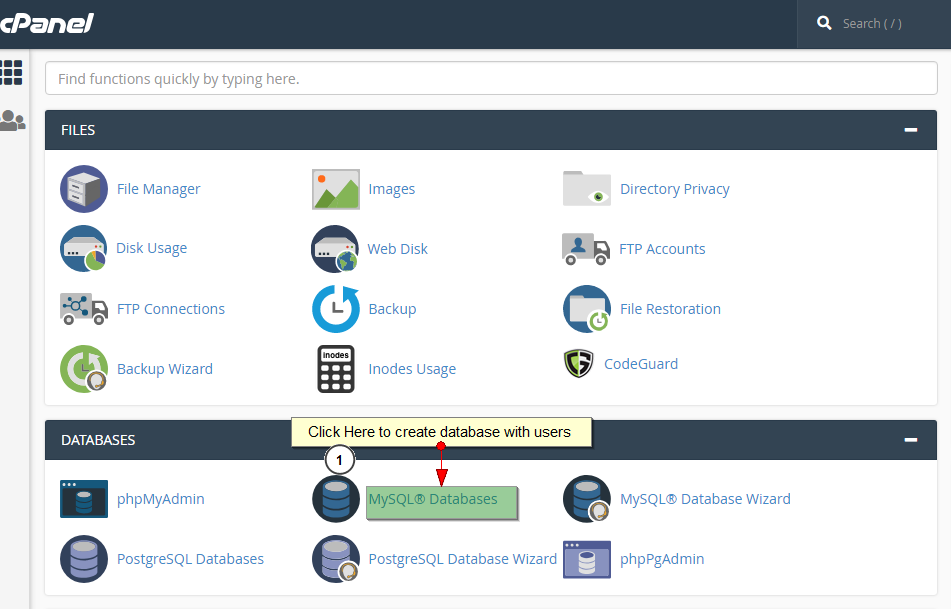
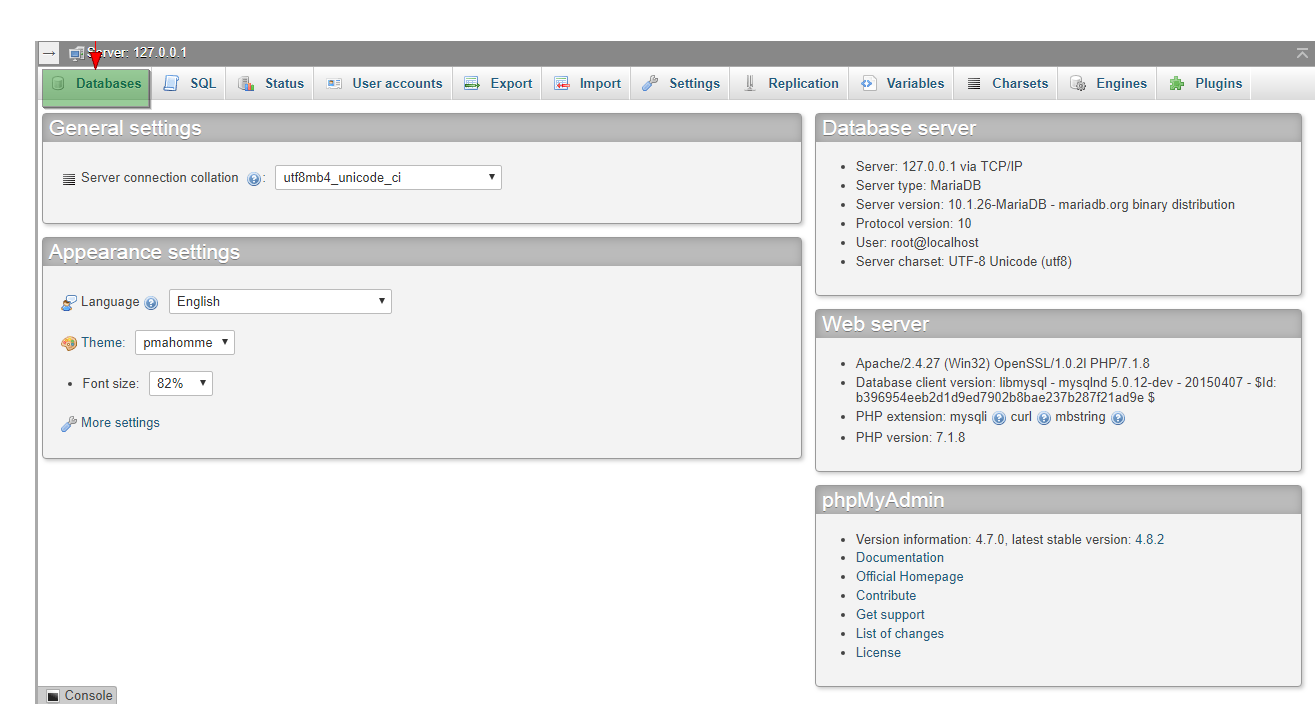
Different PhpMyadmin Utilities and Tools to Master
September 9, 2018 -
How to Create Database and Tables in Phpmyadmin
September 8, 2018 -
Importance of Mobile Friendly Websites
September 7, 2018 -
Top Reasons Why Website Maintenance is Compulsory
September 6, 2018