Website Design Training
-
Stunning Aesthetics with CSS
July 18, 2021 -
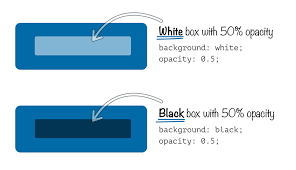
CSS color formats and alpha transparency
July 18, 2021 -
Web typography
July 17, 2021 -
CSS custom properties
July 17, 2021 -
CSS Selectors, Typography, Color Modes, and More
July 16, 2021 -
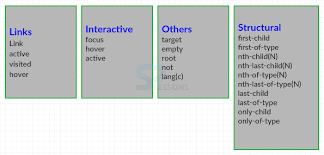
CSS structural pseudo-classes
July 16, 2021 -
Grid with CSS
July 15, 2021 -
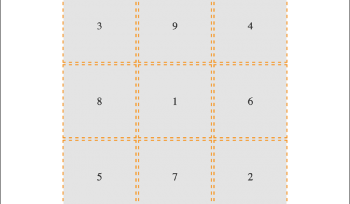
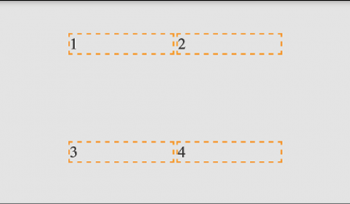
CSS Grid
July 2, 2021 -
cPanel guide and walk through
February 25, 2021 -
How to Install an SSL Certificate on your Website
February 25, 2021 -
Guide on how to Purchase Domain name and Hosting from Soutech Hosting
February 25, 2021 -
How to Become a Front-end Designer
February 25, 2021 -
CyberSecurity and Hacking
August 26, 2020 -
Native Mobile App Development
August 23, 2020 -
Web Development- PHP & MySQL
August 23, 2020 -
Graphics, Branding, UI/UX Design Professional
August 18, 2020 -
MEGA REWARD FOR SOUTECH FACEBOOK TOP FANS!
August 9, 2020 -
Integrating Blogging into a Business Strategy
July 20, 2020 -
WordPress Subdomain | How To Install WordPress On Subdomain? SOUTECH Hosting
October 19, 2019 -
October 2019 Professional IT Training: website design, ethical hacking, digital marketing, data science abuja
October 10, 2019 -
How to Create a Subdomain on SOUTECH Hosting: Top hosting companies in Nigeria
September 28, 2019 -
Step by Step Guide on How to Build a Blog on WordPress: Ultimate Guide 2020
September 26, 2019 -
Choosing a Blogging Platform for your Personal or Business Blog
September 26, 2019 -
Creative ways to promote your business on facebook
August 16, 2019 -
Mata Tags and Meta Keywords – What they are and how to use them for website indexing
August 16, 2019 -
Technical SEO – The best Practice on How To use it to Rank Online
August 16, 2019 -
Social Media Marketing (SMM): The Marketing Essential for Your Business Growth Online
June 28, 2019 -
Front-end Development: A Beginners Guide into Front End development.
June 4, 2019 -
Guide: How to Earn in Website Development Business
May 29, 2019 -
Effective Ways to Optimize your WordPress Website Using Free Plugins
May 29, 2019 -
WordPress Security: Top Five plugins you must have to secure your website
May 28, 2019 -
CMS Website Development: How to Install WordPress on Local Server
May 28, 2019 -
Top 10 Reasons to Choose Content Management System (CMS) for Web Development
May 25, 2019 -
Guide: How to Start and Maintain Your Own Website Design Business
May 25, 2019 -
digitalowerri
May 16, 2019 -
10 Skill-Set Every Successful Website Designer Should Know
May 9, 2019 -
8 Important Plugins to Install for Your WordPress Website
April 29, 2019 -
Popular Types of Web Hosting for Website Designers
April 26, 2019 -
How to Project Manage Your Web Development Application from Start to Finish
February 8, 2019 -
Alert ! Top 5 Reasons Why You Need To Update Your Website Now
November 29, 2018 -
5 Ways to Make Money With WordPress (Themes and Plugins Development)
November 23, 2018 -
10 New Reasons to Have a Website and Why You Should Learn Website Design
October 29, 2018 -
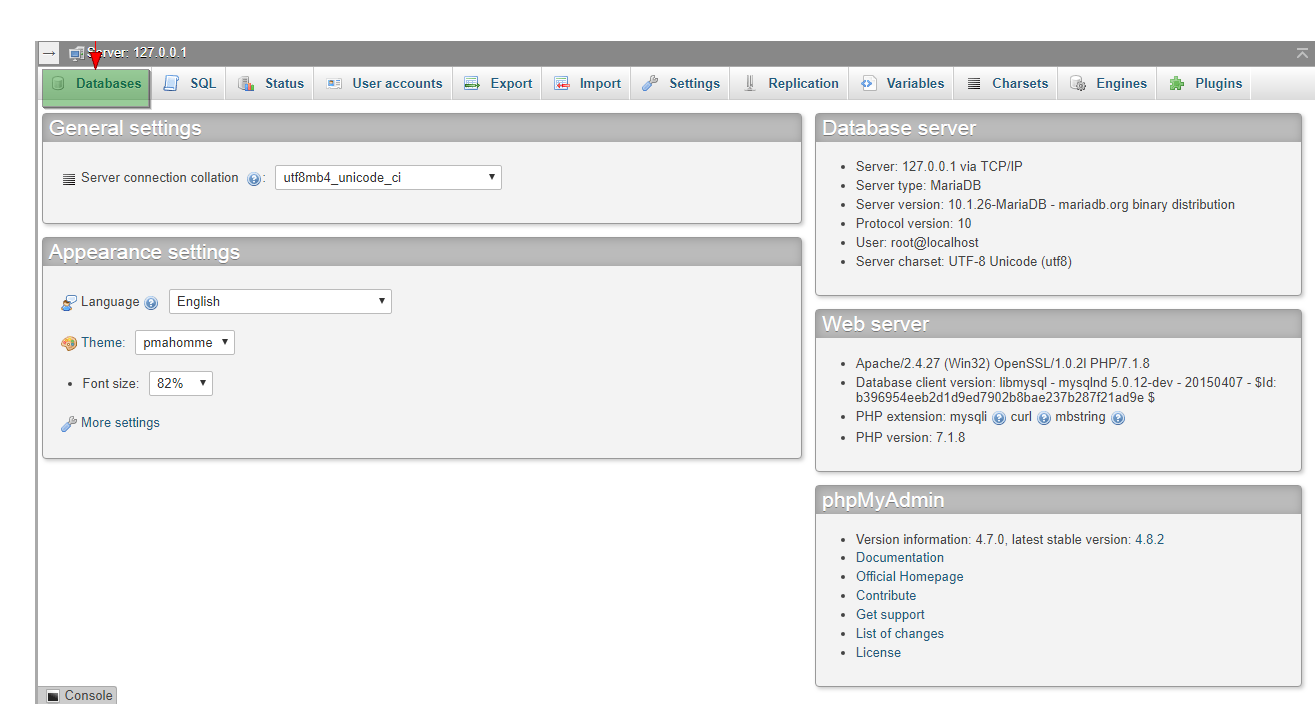
Different PhpMyadmin Utilities and Tools to Master
September 9, 2018 -
How to Create Database and Tables in Phpmyadmin
September 8, 2018 -
Importance of Mobile Friendly Websites
September 7, 2018 -
Top Reasons Why Website Maintenance is Compulsory
September 6, 2018 -
I want to create an amazing and money making blog guide!
August 29, 2018 -
Website Design Training: See this Amazing Corporate and e-Commerce Website Built by a Student.
August 27, 2018